This built-in cyber culture will protect information assets, controls, and processes against a violation of the organization’s business and reputation.
This is an exclusive article series conducted by the Editor Team of CIO News with Kavitha Srinivasulu, Global Head – Cyber Risk & Data Privacy: R&C BFSI – Tata Consultancy Services (TCS).
A major cybersecurity incident represents a true crisis for any organization in the current threat landscape and in-between emerging technology trends. For every organization, incident response is a critical component of any cybersecurity program that involves identifying, containing, and mitigating the impact of security incidents, such as cyber-attacks, data breaches, and system failures, to maintain robust cyber resilience.
Incident response is not a simple process to document and maintain. There are several challenges that organizations face when responding to security incidents, despite having incident response plans and defined strategies. These issues are related to a few key risks evolving day by day. Let’s explore some of the most common incident response challenges and how organizations can overcome them. The cybersecurity team shall be responsible for establishing incident management strategies that meet or exceed a standard of reasonable cybersecurity practices and building robust response controls to reduce or face emerging cyber risks without business impact. This built-in cyber culture will protect information assets, controls, and processes against a violation of the organization’s business and reputation.
Challenges in facing a cybersecurity incident:
- Setting the right set of guidelines to use during an incident is inadequate.
- Increasing expectations of regulators and the board of directors.
- Lack of preparedness.
- Non-compliance risks from failure to meet data protection and breach notification requirements expose organizations to legal and financial consequences.
- Inadequate resources and a lack of visibility.
- Without a security incident management program, organizations lack preparedness, clear roles, and procedures, leading to confusion and errors during incident handling.
How to protect an organization against cybercrimes or security incidents:
Some of the key steps to protect the organization from getting victimized by cyberattacks or data breaches are:
- Create a robust incident response plan and get it tested regularly to keep it current.
- Strong Passwords and Multi-Factor Authentication
- Secure your devices by enabling proper authorization and authentication access.
- Implement Firewall
- Keep the software up-to-date.
- Implement end-point detection and host-based intrusion technologies.
- Backup data regularly.
- Educate internal employees and third parties to avoid internal threats.
- Conduct security awareness training.
- Conduct simulation tests at planned intervals to increase business resilience.
- Know how to distinguish between fake antivirus offers and real notifications.
Cybersecurity Incident Management Framework:
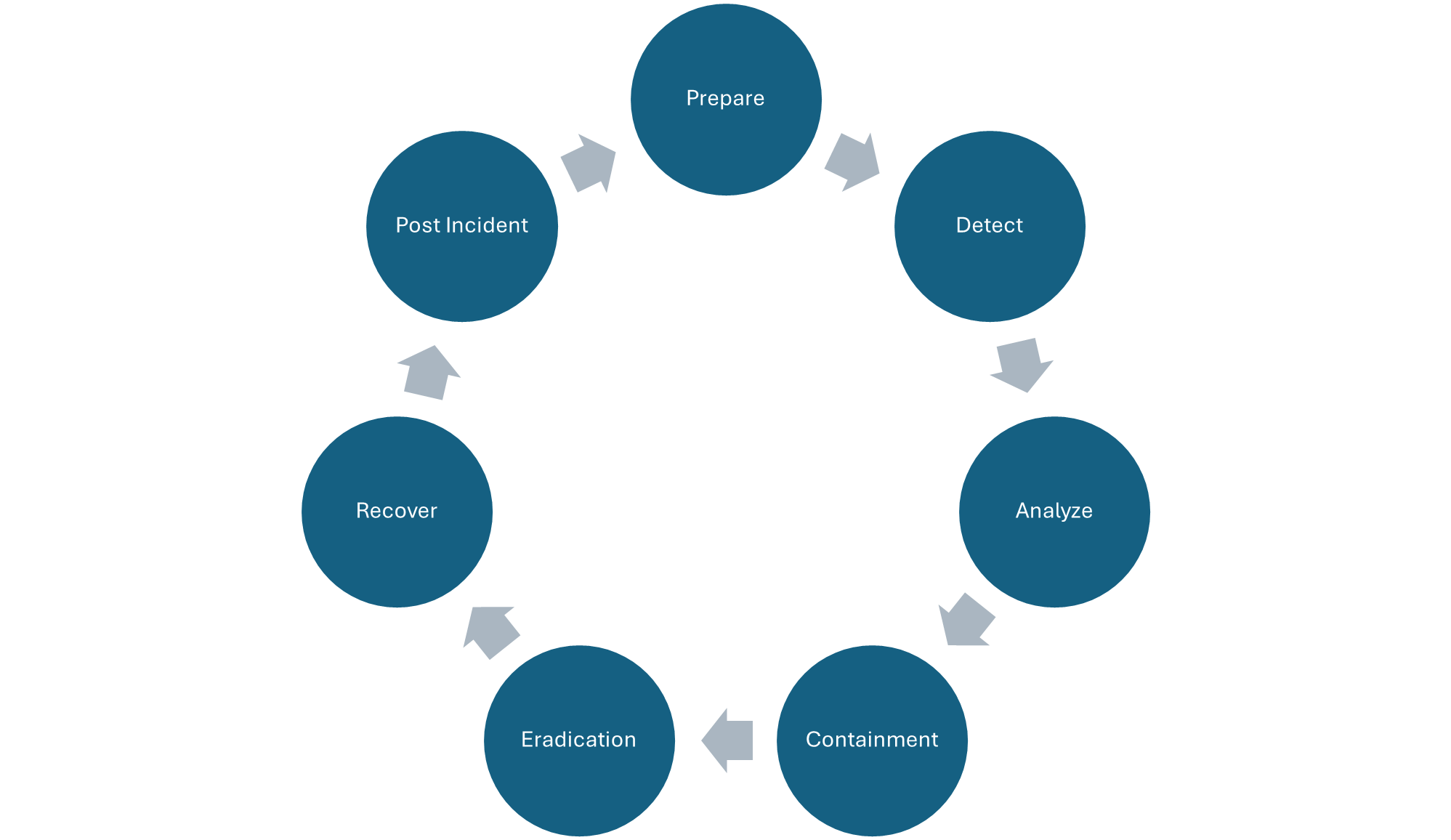
1) Prepare
Initially, identify the sources, people, and technology needed to manage the incident response. Create the workflow by identifying how the security incident can be detected, analyzed, and responded to. Preparation is crucial to effective incident response and reducing the impact on business. Even the best Cyber Security Incident Response Team (CSIRT) cannot effectively respond to an incident without predetermined guidelines. Some of the key actions that need to be considered during the incident response preparation stage are:
- Design, develop, and implement the enterprise-wide incident response plan.
- Create robust communication guidelines to enable effective communication during and after a cyber incident.
- Regular cybersecurity simulation exercises are used to evaluate the effectiveness of the incident response plan.
- Establish a competitive monitoring and response team to handle internal and external threats effectively.
- Ensure there are various ways of continuously educating or training the employees on handling cyber risks or threats.
2) Detect
Determine how the detected threat or incident will be analyzed and resolved. Analyze cybersecurity incidents with a clear objective and as per the defined strategies. The main objective of this stage is to continuously monitor and report on potential security incidents. Conduct cybersecurity incident assessments to detect unknown compromises and remediation steps to ensure the security controls are strengthened to face the security incidents effectively.
3) Analyze
After or prior to any cyber incident, the most important part of understanding the data is analyzing the risks and challenges of the data present in the environment. The majority of the efforts come from analyzing the data and enabling the right set of security controls to ensure business resilience. These efforts also play a critical role in categorizing and classifying the type of cyber incident to increase the effectiveness of response time. Analyze the malicious tools or binaries used by the malicious actor and document the functionalities of those triggers. Document all the compromised systems, devices, and accounts with lessons learned to take proactive measures and avoid future incidents.
4) Containment
This is one of the most critical and important stages of an incident. The approach taken during the containment phase is based on the intelligence and indicators of compromise gathered during the analysis phase. The security team should take diligent steps to prevent further damage, and there is a risk-mitigating action to be taken in a timely manner to avoid business impact on the organization.
5) Eradication
During any incident, one of the important actions is to eradicate the identified malicious actors. An immediate action needs to be taken on the affected systems, domains, or IP addresses connected to the network and leveraged by the malicious actors for command and control to issue ‘threat mitigation requests’ to block the communication from all channels connected to these domains. The incident management team should ensure that the network is isolated without business impact and work effectively with the business functions or respective stakeholders.
6) Recovery
During the recovery phase, the incident management team will play a vital role in invoking response plans as per the processes and procedures for recovery and full restoration of any systems, devices, or accounts during the cyber incident. In the recovery phase, the incident management team will restore systems to normalcy and ensure that the systems are functioning normally. They also work on remediating the gaps identified and vulnerabilities prevailing in the environment to prevent similar incidents.
A critical cybersecurity incident can create a huge business impact for an organization, which would be very hard to recover and resume. However, with appropriate planning and preparation, the organization will be able to efficiently respond to and recover from a cyber incident without major impacts. Maintaining a robust incident response plan and defined business strategies will help minimize the impact of the incident as much as possible.
About Kavitha Srinivasulu
Kavitha Srinivasulu is an experienced cybersecurity and data privacy leader with over 20 years of experience focused on risk advisory, data protection, and business resilience. She has demonstrated expertise in identifying and mitigating risks across ISO, NIST, SOC, CRS, GRC, RegTech, and emerging technologies, with diverse experience across corporate and strategic partners. She possesses a solid balance of domain knowledge and smart business acumen, ensuring business requirements and organizational goals are met.
Disclaimer: The views and opinions expressed by Kavitha in this article are solely her own and do not represent the views of her company or her customers.
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News is the premier platform dedicated to delivering the latest news, updates, and insights from the CIO industry. As a trusted source in the technology and IT sector, we provide a comprehensive resource for executives and professionals seeking to stay informed and ahead of the curve. With a focus on cutting-edge developments and trends, CIO News serves as your go-to destination for staying abreast of the rapidly evolving landscape of technology and IT. Founded in June 2020, CIO News has rapidly evolved with ambitious growth plans to expand globally, targeting markets in the Middle East & Africa, ASEAN, USA, and the UK.
CIO News is a proprietary of Mercadeo Multiventures Pvt Ltd.






