The exploitation likely involved an attack from the VeeamHax folder on the file server against the vulnerable version of Veeam Backup & Replication software installed on the backup server.
CXO DIGITAL PULSE.COM, July 11, 2024: A recently patched security flaw in Veeam Backup & Replication software is being exploited by a new ransomware operation called EstateRansomware.
Group-IB, a cybersecurity firm based in Singapore, discovered the threat actor in early April 2024. The attack leverages the vulnerability CVE-2023-27532 (CVSS score: 7.5) to conduct its malicious activities.
Initial access to the target environment was facilitated through a Fortinet FortiGate firewall SSL VPN appliance using a dormant account.
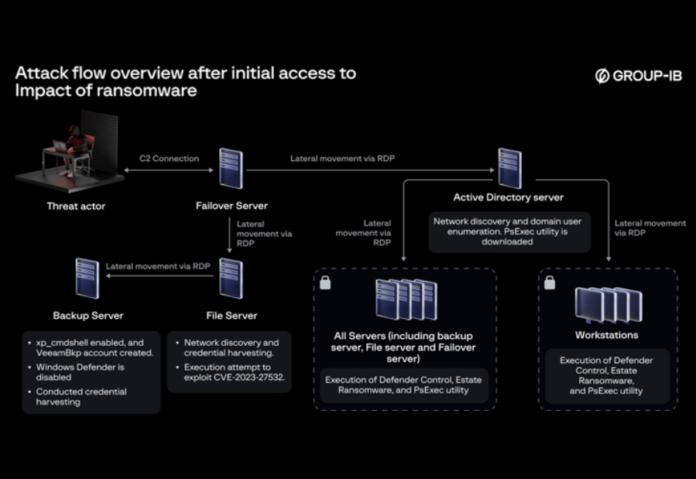
“The threat actor pivoted laterally from the FortiGate Firewall through the SSL VPN service to access the failover server,” security researcher Yeo Zi Wei explained in an analysis published today.
Before the ransomware attack, VPN brute-force attempts were observed in April 2024 using a dormant account identified as ‘Acc1.’ A successful VPN login using ‘Acc1’ was traced back to the remote IP address 149.28.106[.]252.
The attackers then established RDP connections from the firewall to the failover server and deployed a persistent backdoor named “svchost.exe,” which is executed daily through a scheduled task.
Subsequent network access was achieved using the backdoor to avoid detection. The backdoor’s primary function is to connect to a command-and-control (C2) server over HTTP and execute arbitrary commands from the attacker.
Group-IB observed the threat actor exploiting the Veeam flaw CVE-2023-27532 to enable xp_cmdshell on the backup server and create a rogue user account named “VeeamBkp.” They also conducted network discovery, enumeration, and credential harvesting using tools like NetScan, AdFind, and NitSoft through the newly created account.
“The exploitation likely involved an attack from the VeeamHax folder on the file server against the vulnerable version of Veeam Backup & Replication software installed on the backup server,” Zi Wei suggested. “This activity facilitated the activation of the xp_cmdshell stored procedure and subsequent creation of the ‘VeeamBkp’ account.”
The attack culminated in the deployment of the ransomware, following steps to disable defenses and move laterally from the AD server to other servers and workstations using compromised domain accounts.
“Windows Defender was permanently disabled using DC.exe [Defender Control], followed by ransomware deployment and execution with PsExec.exe,” Group-IB stated.
Cisco Talos recently revealed that most ransomware gangs prioritize gaining initial access through security flaws in public-facing applications, phishing attachments, or breaching valid accounts. They also focus on circumventing defenses to increase their dwell time in victim networks.
The double extortion model, which involves exfiltrating data before encrypting files, has led to the development of custom tools (e.g., Exmatter, Exbyte, and StealBit) to send confidential information to attacker-controlled infrastructure.
These e-crime groups often establish long-term access to explore the environment, understand the network’s structure, locate resources to support the attack, elevate their privileges, blend in, and identify valuable data to steal.
“Over the past year, we have witnessed significant changes in the ransomware space with the emergence of multiple new ransomware groups, each exhibiting unique goals, operational structures, and victimology,” Talos noted. “The diversification highlights a shift toward more boutique-targeted cybercriminal activities, with groups such as Hunters International, Cactus, and Akira carving out specific niches and focusing on distinct operational goals and stylistic choices to differentiate themselves.”
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News is the premier platform dedicated to delivering the latest news, updates, and insights from the CIO industry. As a trusted source in the technology and IT sector, we provide a comprehensive resource for executives and professionals seeking to stay informed and ahead of the curve. With a focus on cutting-edge developments and trends, CIO News serves as your go-to destination for staying abreast of the rapidly evolving landscape of technology and IT. Founded in June 2020, CIO News has rapidly evolved with ambitious growth plans to expand globally, targeting markets in the Middle East & Africa, ASEAN, USA, and the UK.
CIO News is a proprietary of Mercadeo Multiventures Pvt Ltd.