
This is an exclusive article series conducted by the Editor Team of CIO News with Vishwas Pitre, VP – Chief Information Security Officer (CISO) & Data Privacy Officer (DPO) at Zensar Technologies Ltd.
According to Cybersecurity Ventures, the cost of cybercrime worldwide is projected to reach $8 trillion (about $25,000 per person in the US) in 2023, and it is expected to grow to $10.5 trillion (about $32,000 per person in the US) by 2025. This represents a significant increase from the $6 trillion (about $18,000 per person in the US) in 2021, underscoring the escalating nature of cyber threats. This cost averages out to around $24,000 per person in the U.S. in 2023, reflecting the deepening financial burden that cybercrime imposes on both individuals and businesses.
As per reports published by EFFICIENTIP in August 2023 titled: 2023 Global DNS Threat Report [1], 90% of companies experience DNS attacks, out of which 73% experience downtime. The report also revealed that organizations in the financial services sector suffer the highest cost per DNS attack, compared to organizations in other industries.
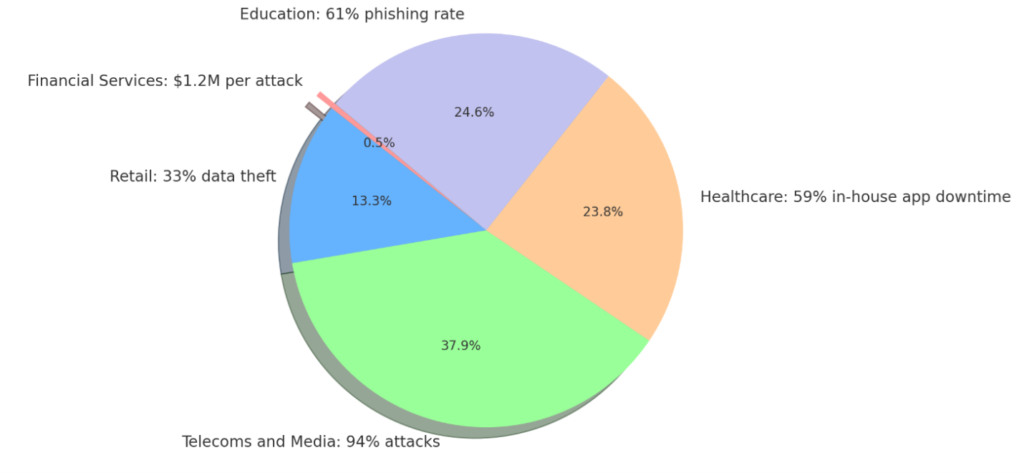
Figure 1. DNS Attacks percentage on Various Industries
The number of companies that suffered DNS-based attacks has increased, growing 4.29% over 2023 and reaching an alarming 90% in 2023.
DNS[2] is one of the most important services for communication that happens over the internet/intranet. As today’s communication relies too much on DNS, it becomes one of the primary targets for hackers/attackers to exploit the loopholes associated with DNS communication. The report [1] also quoted: “DNS is critical to ensure service continuity. Faulty or ineffective DNS services can negatively affect the perception of any organization (from clients, partners, or employees), impact your e-commerce applications, resulting in lost revenue, and ruin a brand image.”.
What is DNS?
DNS, an acronym for Domain Name System, often referred to as Domain Name Server, can be treated as a phonebook on the internet. All the communication that happens over the internet is based on Internet Protocol (IP) and Address Resolution Protocol (ARP). Each resource over the internet is accessed by Internet Protocol Address (considering the IPv4 mechanism), which is of the 32-bit address. It is very difficult for the human mind to access resources over the internet via Internet Protocol Address. Say, for example, the official URL of XYZ Technologies is supposed to be accessible using: https://X.X.X.X (need to proceed with accepting the risk as the browser will throw an SSL Certificate mismatch error), as it is very difficult to remember the accessible link using an IP address. So, what is the solution for this? Well, the answer to this is having a Domain Name System (DNS), like www.xyz.com, which is internally mapped with IP address X.X.X.X. Whenever any user requests the website www.xyz.com, in the background the DNS name is being converted to an IP address and the resource, https://X.X.X.X, is being accessed by the user. Figure 2. shows the working of the DNS Concept at the abstract level.
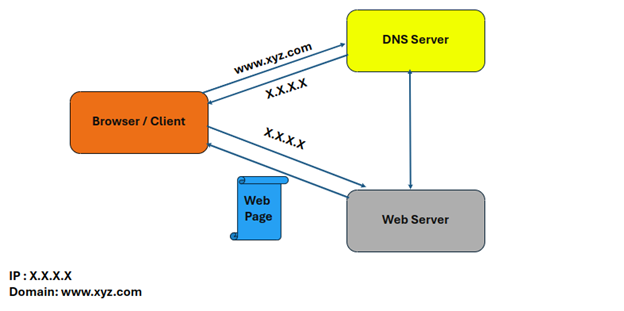
Figure 2. Working of DNS
DNS cache poisoning attack
There are several types of DNS-based attacks that, over the past, have caused severe damage to banking and financial organizations. The most common out of them is DNS cache poisoning [3] (often termed DNS spoofing), which can redirect the actual request to some malicious websites (which can compromise the end-user system) or fake websites (which might appear to be the same website as that of the requested website). This kind of attack can be dangerous, especially if bank login credentials or debit/credit card information is being entered. Fake websites can also install malicious viruses, worms, or Trojans into the end-user’s system.
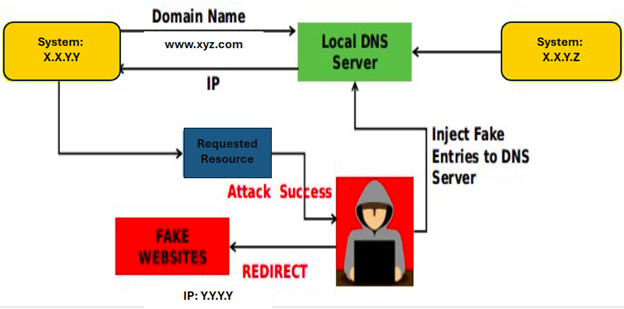
Figure 3. DNS Cache Poisoning Attack
Explanation: Refer to Figure 3. The client had requested some websites, www.test.com, which should access the resource X.X.Y.Z, but somehow the DNS server is compromised, and the attacker has successfully injected a fake entry for www.xyz.com. In this case, the request will be routed to System Y.Y.Y.Y.
Blockchain and machine learning as a scope and solution to DNS cache poisoning attacks (primarily explaining the uniqueness of blockchain technology):
Blockchain is one of the emerging technologies of the recent era that can play a vital role in mitigating many cybersecurity reported issues that exist today.
DNS is an unencrypted protocol. To make it more secure, DNSSEC [4] has been introduced. While DNSSEC is an encrypted protocol, it still has two major drawbacks:
- Complex Deployment: DNSSEC has not yet become a mainstream protocol and is often misconfigured, which sometimes denies access to the requested webpage and can cause the server to lose the security benefits altogether.
- Lack of Data Confidentiality: DNSSEC authenticates but doesn’t encode DNS responses. As a result, perpetrators are still able to listen in on traffic and use the data for more sophisticated attacks.
Prevention using Blockchain:
Figure 4. shows the proposed methodology to prevent DNS servers using encryption, added with user-defined ports.
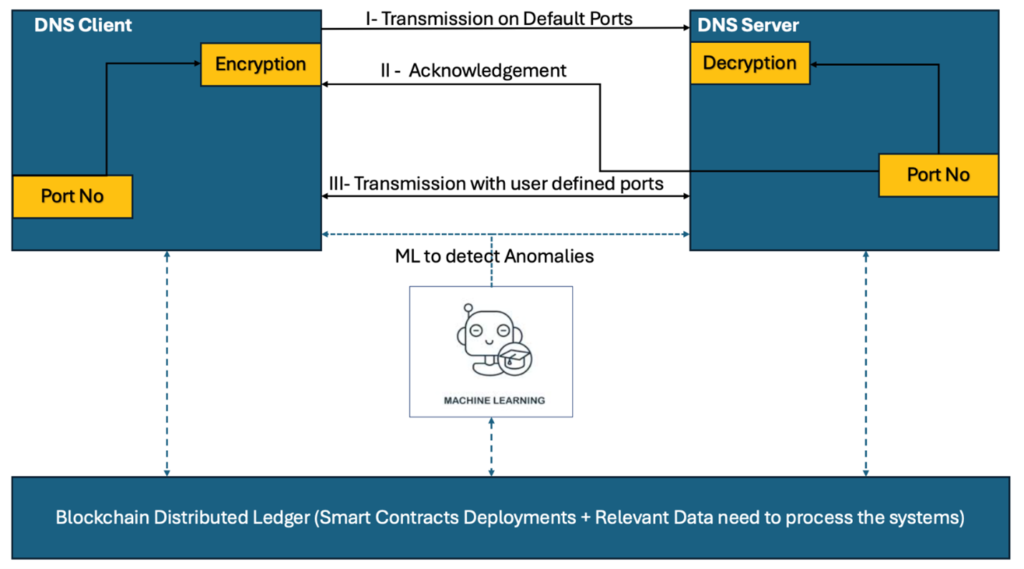
FIGURE 4. Block Diagram of the proposed system.
Phase 1: Blockchain-Based Registration and Encryption
- Blockchain for Registration:
- Blockchain Ledger: Register DNS servers and clients on a blockchain ledger. Each DNS server and client has a unique blockchain identity, which includes their public key and other identifying details. This ensures that only legitimate DNS servers and clients can communicate.
- Port and IP Address Encryption:
- The client generates a random port number (outside the 0-1023 range) and pairs it with its IP address.
- This data (IP + port) is encrypted using the client’s private key and sent to the DNS server via a secure channel (e.g., HTTPS).
- The predefined port (e.g., 80 for HTTP) is used for the initial communication, and blockchain authentication ensures the integrity and authenticity of the DNS server and client.
Phase 2: Decryption and Verification Using Blockchain
- Blockchain-Based Decryption and Verification:
- Decryption: The DNS server decrypts the received data (IP + port) using the client’s public key obtained from the blockchain.
- The DNS server checks the client’s identity against the blockchain ledger to ensure the request is legitimate and has not been tampered with.
- Acknowledgment: Once verified, the DNS server sends an acknowledgment back to the client using its own private key, confirming that the transmission will proceed with the user-defined port.
- Machine Learning for Anomaly Detection:
- The DNS server runs a machine learning (ML) model trained on normal DNS request patterns to detect any anomalies that could indicate potential threats or attacks.
- If the ML model detects unusual patterns, such as repeated requests from unusual ports or IP addresses, the server can trigger additional verification steps or reject the request.
Phase 3: Secure Data Transmission with Dynamic Port Management
- Blockchain-Enhanced Communication:
- The client initiates the actual data transmission on the user-defined port, which was securely exchanged during Phase 1.
- Smart contracts for dynamic port management:
- Smart contracts on the blockchain can manage the lifecycle of user-defined ports, including assigning, releasing, and monitoring their use.
- If a smart contract detects any irregularities in port usage, it can dynamically change the port to prevent potential MitM attacks.
- Continuous Machine Learning Monitoring:
- Throughout the communication, machine learning models continuously monitor for signs of DNS cache poisoning, MitM attacks, and other malicious activities.
- The models can use real-time data and historical patterns to predict and prevent attacks before they fully materialize.
- Any suspicious activity is immediately flagged, and communication can be halted or rerouted as necessary.
Figure 5. shows how the DNS cache poisoning will be prevented by the proposed architecture.
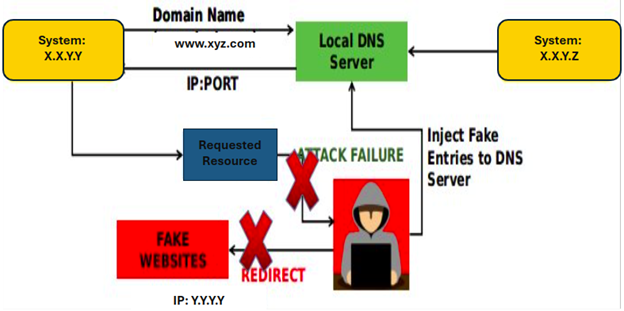
Figure 5. DNS Cache Poisoning Attack Failure with Proposed System
Refer to Figure 5. In this scenario, the attacker will be unable to determine which port the attack should target. Even if the request is intercepted, the attacker won’t possess the C/O decryption key, preventing them from viewing the request. Consequently, the attacker won’t be able to acknowledge the user (X.X.Y.Y. in our example), and further communication between the client and the attacker will cease. Additionally, every event (or transaction in blockchain terms) occurring on the DNS Server will be logged in the blockchain ledger for auditing purposes. For legitimate traffic, the ML System will detect malicious requests (such as IP reputation, request patterns, etc.), providing an additional layer of security control. This will also assist in identifying any ongoing DNS-based attacks on the network.
Summary:
DNS is more than ever a central network foundation, enabling all clients to access every application. Any DNS performance impact has major business implications. At the same time, the fact that most traffic first goes through a DNS resolution gives it unique visibility over legitimate and malicious network activity.
Blockchain integrated with machine learning techniques can help organizations save millions of dollars each year by encrypting the data and preventing hackers from accessing it. This can be one of the ways organizations can strengthen their DNS defenses. This type of defense is especially critical for the banking and financial sector businesses, which are being targeted more and have more to lose in terms of reputation and financial implications.
References:
- https://efficientip.com/wp-content/uploads/2023/09/IDC-2023-DNS-Threat-Report.pdf
- https://www.seobility.net/en/wiki/DNS_Server
- Son, Sooel; Shmatikov, Vitaly. “The Hitchhiker’s Guide to DNS Cache Poisoning” (PDF). Cornell University. Retrieved 3 April 2017
- https://en.wikipedia.org/wiki/Domain_Name_System_Security_Extensions
- https://cybernews.com/resources/what-is-a-dns-attack/
Also read: Unveiling the Ethical Imperatives: Navigating the Intersection of AI and Cybersecurity
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News is the premier platform dedicated to delivering the latest news, updates, and insights from the CIO industry. As a trusted source in the technology and IT sector, we provide a comprehensive resource for executives and professionals seeking to stay informed and ahead of the curve. With a focus on cutting-edge developments and trends, CIO News serves as your go-to destination for staying abreast of the rapidly evolving landscape of technology and IT. Founded in June 2020, CIO News has rapidly evolved with ambitious growth plans to expand globally, targeting markets in the Middle East & Africa, ASEAN, USA, and the UK.
CIO News is a proprietary of Mercadeo Multiventures Pvt Ltd.





