
Skill levels should be mapped on the basis of the operational needs.
This is an exclusive article series conducted by the Editor Team of CIO News with Suresh Vijayaraghavan CTO at the Hindu.
Context: If change is the only constant in the technology domain in general, rapid change is the norm in IT (information technology). Even the approach to information technology management is changing rapidly compared to other management areas. One of the key challenges that organisations face is ensuring that the skill level of their technical team is in line with the developments that are happening within the industry. Even staff are struggling to continuously upgrade themselves to stay relevant.
Most organisations or IT departments are looking forward to a method to
- Identify what skill set is required for their operations!
- What is the current skill set of employees within the organisation?
- How do I identify gaps and fill them?
- How do you continuously monitor and upgrade staff skills?
- Professionally manage the skill set
It is becoming increasingly clear that a process-based approach is needed for skill development planning. In this post, I try to put forward such an approach. While this was primarily developed for IT organisations (or IT departments) and the examples used will be from the IT domain, this approach can be adopted and used anywhere.
Competency Development Process
The approach to competency development is outlined in Fig. 1 and progresses in line with the PDCA model. The phases Identify, Evaluate, and Execute are followed in sequence and continuously on an on-going basis.
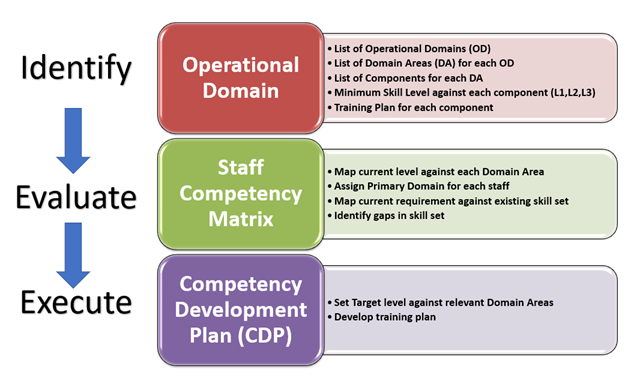
Fig-1
Identify: Operational Domains (OD) -> Domain Areas (DA) -> Components
The whole process is built around the above structure. An operational domain is a boundary that includes more than one domain area, which in turn will contain more than one component. Ultimately, the knowledge and skills that are to be gained are about the component. Based on the size and complexity of the IT operations, the boundary for these can be defined. Using an example, I will explain this concept clearly. In Fig. 1, we see an example where two operational domains have been taken up.
| S.No | Operational Domain | Domain Area | Component | Mapped Skill Level | Competency Details |
| 1 | Windows Server OS | Windows Server 2019 | Active Directory | L2 | Single Domain / multisite/RODC/Child Domain/ Site/Forest/Domain Functional Levels / AD Restoration /Objects/User/Group/ AD 5 Roles / Roles Transfer / Domain Trusts / AD DS Cloning / AD federated Services / AD recycle bin
|
| Group Policy | L2 | Software settings , User settings , Administrative settings
|
|||
| NLB | L3 | Load balancing , Web server load balancer configuration , NLB network card setup
|
|||
| File Services | L2 | user maping scripts , file permissions , File & Print sharing , Spooler creation , manageing the Service request ,
|
|||
| Clustering | L3 | Two Node, Multi Node | |||
| Rights Management | L3 | AD- RMS , Creating Services using AD RMS , Assigning rights using ADRMS
|
|||
| 2 | Networking | Switching | Layer-3 Switching | L2 | Inter-VLAN Routing |
| Layer-2 Switching | L2 | VLAN | |||
| Routing | BGP | L3 | Autonomous Systems |
Fig-2
Depending on the complexity of IT operations, we can either shift left or shift right within the OD, DA, and component. For example, in Fig. 2, we have shifted right to create the server operating system itself as an OD.
| S.No | Operational Domain | Domain Area | Component | Mapped Skill Level | Competency Details |
| 1 | Server OS | Windows Server | Installation & Configuration of AD | L1 | Single Domain / multisite/RODC/Child Domain/ Site/Forest/Domain Functional Levels / AD Restoration /Objects/User/Group/ AD 5 Roles / Roles Transfer / Domain Trusts / AD DS Cloning / AD federated Services / AD recycle bin
|
| File Services | L2 | Setup a network file server | |||
| Linux Server | LAMP Stack | L2 | Implement a LAMP stack | ||
| Clustering | L2 | Setup Linux Cluster |
Fig – 3
Mapped Skill Level: This also depends on the complexity of IT operations, where a certain skill may be mapped as L1 in certain places and L2 in others. This allows the organisation to map skill levels based on their operational needs.
Note that these are examples to explain how to use the OD->DA->Component triad, and these can be setup in numerous ways as per the requirements. That is the uniqueness of this model.
Evaluate
Now that we have defined the requirements, the next step is to map each employee against their skill level for each OD/DA. Each member must also be assigned a primary domain. Their skill level in the primary domain will be their key capability. This provides us with the staff competency matrix (Fig. 4). This activity gives an overall picture of the current competency landscape in the organisation.
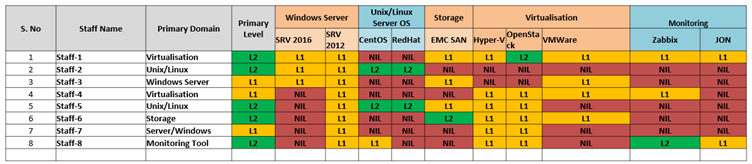
Fig-4 – STAFF COMPETENCY MATRIX
By mapping the resource requirements against what is there within the organisation, the current gaps can be identified (Fig. 5). This can also be used to plan a shift schedule to ensure balanced skill set availability at any time.
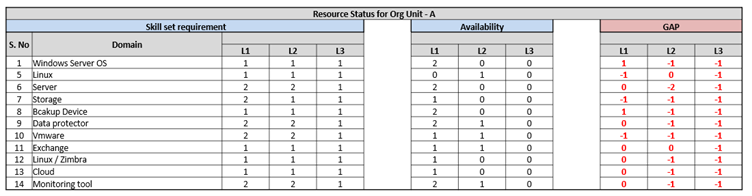
Fig-5: Skillset Gap Identification
Execute
The above activities will help identify the gaps in the needed skillset. Now we can set for each OD->DA a target skill level for each employee based on their current level. By using the component list, a training plan can be devised. As employees progress in their skill development, the skill matrix must be updated so that it reflects the status accurately.
Continuous Improvement
As with any process-based approach, unless we have an ongoing continuous improvement strategy, it will become stale or obsolete very soon. As shown in Fig. 5, organisations can review each aspect of this model periodically to ensure that they can benefit continuously from this approach.
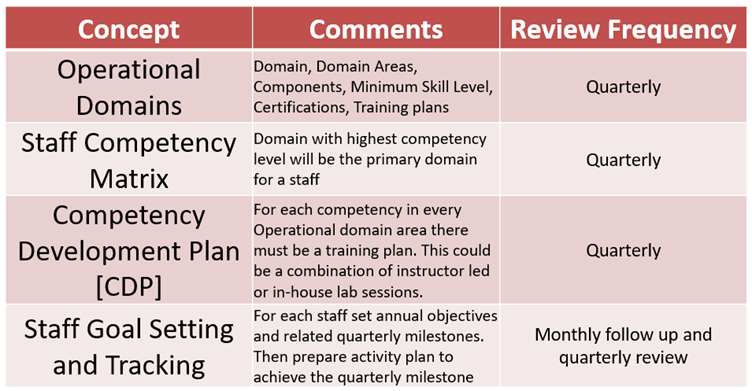
Fig-5: Periodic Review
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics.





