Strategies for mitigating ransomware threats must be a top priority for every organization.
CIO News is releasing an exclusive article written by Kavitha Srinivasulu, Global Head – Cyber Risk & Data Privacy: R&C BFSI at TCS.
About Kavitha: Kavitha Srinivasulu has around 20 years of experience focused on cybersecurity, data privacy, and business resilience across BFSI, financial services, retail, manufacturing, health care, IT services, and telecom domains. She has demonstrated her core expertise in risk advisory, business consulting, and delivery assurance with diverse experience across corporate and strategic partners. She is a natural leader with the versatility to negotiate and influence at all levels. The views and opinions expressed by Kavitha in this article are only from her personal side and do not represent her company’s viewpoints or share any of her customers views.
Ransomware is the fastest-growing cybercrime and is creating lots of uncertainty in today’s threat environment. A report from Cybersecurity Ventures estimates that there was one ransomware attack every 11 seconds and estimates that around 4,000+ ransomware attacks occur daily across the globe. Looking at the volume of these attacks and the deep attack surface connections between organizations and their third parties, there’s a high possibility of leaked personal data leading to big threats evolving across various sectors. The leaked credentials are the keys to the corporate network, which could put them at risk of losing important and confidential information.
A ransomware attack is the most expensive and disruptive incident that impacts businesses at a high level. It takes lots of effort, a high ransom, and huge data compromises while struggling to return to normalcy. Ransomware is primarily a sophisticated type of malware that can infect a computer, system, laptop, or mobile device and subsequently hold sensitive data or personally identifiable information (PII) hostage until a price, or “ransom,” is paid. Cybercriminals often use a binary encryption key to restrict data access to extort money from victims or lock the victim’s system or network to stop access to the data and demand a high ransom to restore vital information.
Ransomware attacks can be especially dangerous for businesses, hospitals, schools, or other organizations that rely on that information to function daily. In most cases, failure to pay the ransom can lead to permanent loss or exposure of confidential data that would end up causing the business to shut down. Hence, a robust and vital zero-trust approach is needed where you can detect and respond to ransomware by proactively managing your cybersecurity risks, identifying vulnerabilities, and minimizing the impact of attacks.
Some of the most common ways ransomware attacks are raised are:
- Deceptive phishing emails
- Visiting corrupted websites
- Downloads from malicious websites
- Using unsecured public Wi-Fi
- Opening or downloading infected file extensions or malicious attachments
- System and network vulnerabilities
- Remote desktop protocol (RDP) attacks
The Lifecycle of a Ransomware Attack –
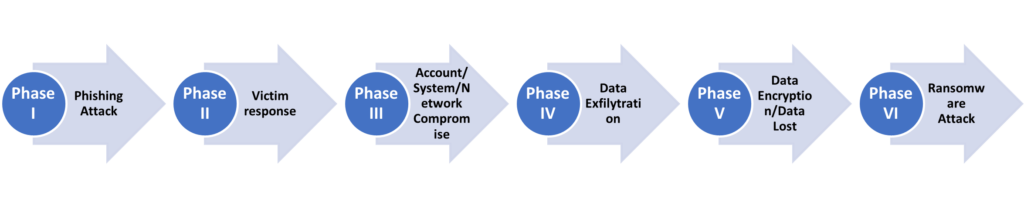
An effective ransomware attack happens in a phased manner, targeting the victim to get hold of PII data. A ransomware attack lifecycle is comprised of eight key phases:
Phase 1: Phishing Attack
An email looking like a legitimate message from an authoritative sender is sent to a victim. It tricks the victim and targets some kind of action from the end user. These emails include malicious links or attachments to steal internal credentials. Phishing emails are the most prevalent type of attack used by predators to initiate data breaches.
Phase 2: Victim System Access
Once the victim acts on the email received, access is enabled for the predator.
Phase 3: Account Compromise
The victim compromises corporate credentials either by clicking on the links in the email or by opening the attachments, falling victim to a phishing attack.
Phase 4: Data Hunting
Cyberattackers identify and compromise privileged corporate credentials to hunt for sensitive or personal data.
Phase 5: Privilege Escalation
After getting access to the system, cybercriminals start targeting it to gain access and intrude on the network.
Phase 6: Data Exfiltration
When highly confidential and critical data resources have been located, cybercriminals set up trojan malware to establish backdoor connections to encrypt or lock the data. Data extortion tactics help the predators coerce victims to pay their demanded ransom.
Phase 7: Data Encryption
Ransomware criminals encrypt the victim’s operating systems and computer systems with the objective of inflicting maximum business disruption.
Phase 8: Data Dump
The final phase of the ransomware attack is the data dump. This is where predators expose compromised data in a cybercriminal marketplace to generate revenue.
Recent studies confirm that having strategies for mitigating ransomware threats must be a top priority for every organization. Some of the actions that can be taken by organizations to prevent potential malware and ransomware attacks are:
- Action 1: Regular backups to ensure data protection.
- Action 2: Prevent malware or suspicious emails from being delivered to inboxes and spreading to devices.
- Action 3: Continuous Monitoring
- Action 4: Proactive Incident Management Planning and Testing
Every organization, irrespective of size, geography, and spread, is becoming a potential target for ransomware attacks. Safeguarding from ransomware attacks has been a top concern in recent times. Understanding and protecting customer data is vital to sustaining business. Some of the industry best practices (prepare, react, and recover) to ensure your organization is prepared for these attacks and resilient in nature are:
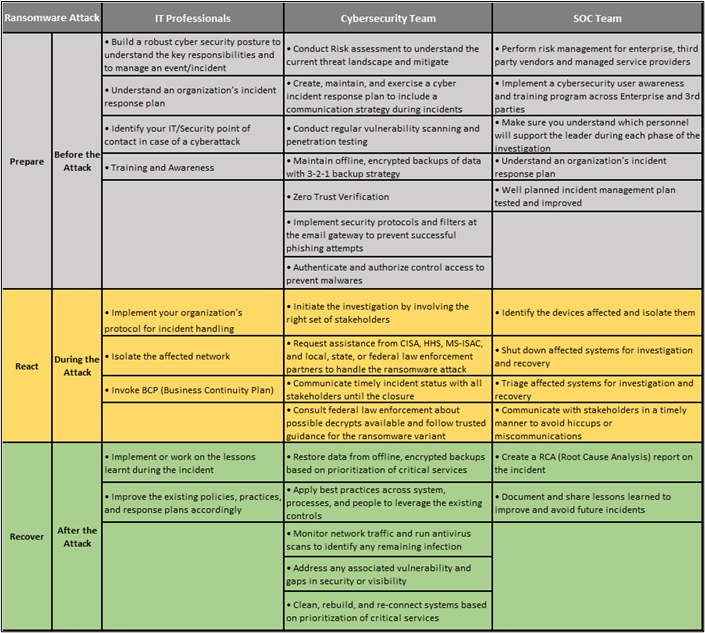
Ransomware Prevention Checklist:
- Maintain good backups of files: Backup files should be appropriately secured and stored offline to ensure that they have no access to external traffic or predators.
- Deploy email filtering: Block malicious traffic, phishing emails, spam, and other unwanted communications to avoid becoming a victim of ransomware.
- Robust Incident Response Plan: Create an incident response plan to be planned, and let the organization know what to do during a ransomware event.
- Have an Intrusion Detection System: Avoid ransomware attacks by enabling a continuous monitoring system to detect malicious or anomalous activities in the early stages and take proactive measures before they spread.
- Whitelist Applications: Have whitelist software enabled to whitelist the authorized applications and avoid any unauthorized programs running in the background.
- Harden your endpoints. We need to ensure systems are configured with the right set of security measures to strengthen the security posture and avoid unauthorized traffic.
- System monitoring: All the operating systems, applications, and software are upgraded, revised, and updated on a regular basis to avoid evolving vulnerabilities. Always ensure all firewalls are secured and operational.
- Ransomware Attack Testing (Security Simulations, Data Breach Attacks, and Phishing Email Testing): Conduct a simulation to ensure the teams and end users are aware of the ransomware attacks and how to handle them.
- Training and Awareness: Cybersecurity Training and awareness are two of the key pillars to preventing ransomware attacks and avoiding becoming a sole victim. Conduct security awareness training and educate your end users about ransomware attacks.
Ransomware attacks are one of the most threatening attacks on organizations today. As more ransoms are paid to restore data, some of the cases are compromised without being able to manage to compensate for the predator’s demand. While organizations are increasing their expenses on cybersecurity and data protection solutions to prevent ransomware and other cyberattacks, it is essential for them to increase awareness and train their resources to handle the threats in an effective manner.
Also read: Organizations should be driven based on people and processes instead of emphasizing technology
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics.






