The Omicron variant has a much higher transmission rate, and as a result, daily counts of new Omicron patients have become a global concern.
This has again renewed heightened concern about the pandemic, and cyber threat actors don’t shy away from using the situation to their advantage.
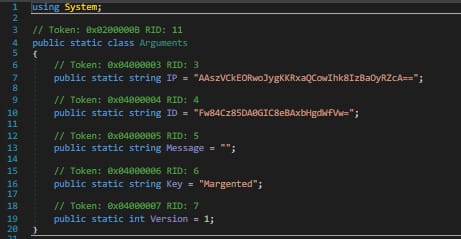
FortiGuard Labs recently came across a curiously named file, “Omicron Stats.exe”, which turned out to be a variant of Redline Stealer malware. The first reports of RedLine Stealer go back to March 2020 and it quickly became one of the most popular infostealers sold in underground markets. The Information harvested by RedLine Stealer is sold on the dark net marketplace for as low as 10 US dollars per set of user credentials. The malware emerged just as the world began to deal with increased numbers of COVID patients and the growing fear and uncertainty that can cause people to lower their guard, which may have prompted its developers to use COVID as its lure.
Normally, victims whose systems have been infected with this stealer unknowingly have their account passwords and full browser details recorded, and then sent to marketplace operators. Generally, in such cases, each compromised user profile includes login credentials for accounts on online payment portals, e-banking services, file-sharing or social networking platforms.
The file name of this current variant, “Omicron Stats.exe,” was used just as the Omicron variant was becoming a global concern, following the pattern of its previous variants. FortiGuard Labs has concluded that email is the infection vector for this variant as this malware is embedded in a document designed to be opened by the victim. Based on the information collected potential victims are spread across 12 countries. The information that it steals can be used for malicious actions by the same cybercriminal or sold to another threat actor for future activities.
Advices Rajesh Maurya, Regional Vice President, India & SAARC at Fortinet “Stay outside of the red zone by exercising basic security practices. Look at the sender’s email address before clicking on emailed links or downloading attachments, even if they appear to come from a trusted source. In most cases, phishing emails are sent from addresses that do not contain the supposed sender’s organization’s legitimate web address. Educate employees, family members, and friends about what to avoid and keep devices updated with the latest security software.”
Also read: CIO News interviews Shri Wangki Lowang, Minister (IT) of Arunachal Pradesh
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics.