My advice to corporate cyber security teams is to go to their plants, understand the process well, learn the language of the OT people, and build relationships with them, as this will help in tackling cyber security concerns more efficiently
This is an exclusive interview conducted by the Editor Team of CIO News with Mohamad Mahjoub, Chief Information Security Officer (CISO) at Veolia Middle East
I have been the CISO of the Near and Middle East region for the past three years. With the acquisition of SUEZ’s business in the area, IT and OT challenges are inevitable, and opportunities abound.
My areas of expertise are IT/OT governance, data protection, cloud security, risk management, and application security. I have more than 17 years of experience in IT with a focus on cyber security. I am the author of the book “Ethical Hacking with Kali Linux Made Easy”, which is published on Amazon, as well as many online Cyber Security courses, some of which are sponsored by Packt and O’Reilly. That’s on top of being an active YouTuber on ethical hacking topics.
Hats off to the industrial community who made extraordinary efforts to keep civilization running under the challenging circumstances of COVID-19 pandemic and even post-pandemic, which in turn resulted in many industrial entities shifting their ways of conducting business to espouse, an increasingly connected industrial grid.
Taking this fact into consideration, the trend continues, and cyber-attacks keep on coming with no end in sight. Billions of US dollars have been spent over the past ten years on cyber-attacks. Such attacks exist in the digital space, but today they are having a real and tangible effect on our physical world.
Facilities that aid the economy, public safety, and public health are categorised under the umbrella of critical infrastructure. Due to the exploding digital transformation that has happened in recent years in the critical national infrastructure, there is a path nowadays for attackers to run from spoofed email in an email inbox all the way through the network to the ICS crown jewels and industrial assets. We learned a lot from the recent industrial attacks in 2021 and 2022, including the fact that the initial attack vector is usually simple due to a weak security perimeter, that ransomware gangs are maturing, and that when a critical public service is at stake, the ransom is more likely to be paid.
Critical environments cannot afford to fail. An operational outage of even a few seconds when public safety is at stake is not tolerable. We need to build in cyber resilience so these systems are able to resist and fight back against cyber-attacks. This is why IT and OT are different.
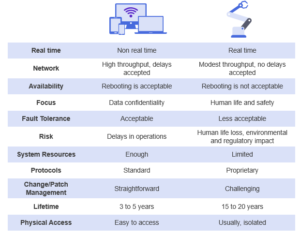
In 2010, Stuxnet was made public. A trojan exposed the vulnerability of industrial environments by attacking the PLCs in control of the centrifuges of an Iranian nuclear enrichment plant. Since this attack, which was caused by an infected USB key, the entire industrial world is at risk from cyberattacks.
Despite the passage of time, cyberattacks’ methods have changed, but industrial control systems in factories continue to be a top target. Taking this into consideration, the trend goes on. Cyber-attacks keep on coming with no end in sight. During the last ten years, billions of dollars have been spent. Cyber-attacks exist in the digital space, but today they can have a real and tangible effect on the physical world. Here are a few of the major incidents that happened after Stuxnet.
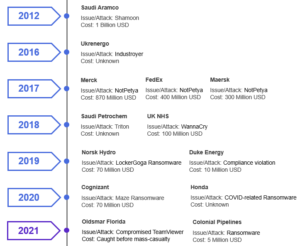
The same evaluation is valid in 2022. The Russian invasion of Ukraine on February 24, 2022, is the first of these risk-changing occurrences. This event increased the likelihood of significant cyber activity involving both the industrial infrastructure of the combatants and ransomware, the name of the game to attack big organisations and governments.
The Ransom Cartel arose a few years back. Twisted Spider, the gang behind Maze ransomware and others, is said to be the group that initiated its creation. Their primary motivation was financial gain. Victim data is not the only thing these affiliate gangs pass between each other; they share tactics, infrastructure (C&C), and offer Ransomware-as-a-Service (RaaS) packages available to other criminals.
To deep dive into one instance, since its release, Ryuk has harmed many manufacturing, healthcare, and governmental entities. The Ryuk gang uses post-exploitation frameworks like Cobalt Strike or PowerShell Empire after a TrickBot (Trojan) infection and the discovery of an intriguing target, which enables them to carry out unwanted actions on machines without invoking security alerts.
The Ryuk attackers also employ BloodHound, a tool that enables penetration testers to examine and identify potentially vulnerable relationships that exist in Active Directory setups, as well as the open-source LaZagne programme to steal passwords stored on infected computers. The Ryuk attackers’ ultimate objective is to locate domain controllers and take control of them, which would give them control over the entire network.

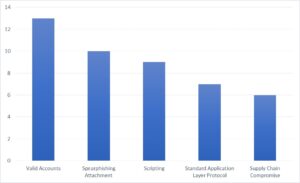
In a study published recently by Dragos, valid accounts are the most common TTP used in attacking ICS systems. Shared credentials and poor security perimeters allow adversaries to leverage valid accounts and gain persistent access to remote ICS.
Critical national infrastructure has undergone a rapid digital transformation in recent years, opening up a channel for attackers to travel from counterfeit emails in an employee’s inbox all the way to the crown jewel assets.
There are several OT problems. A recent study has found a number of third-party weaknesses in the software supply chain of many ICS systems. Most notably were the flaws known as Ripple20 and Amnesia:33, which were third-party Internet Protocol (IP) stack vulnerabilities. These flaws were found in many industrial products, including PLCs, Serial to Ethernet Converters, Protocol Converters, Remote Terminal Units (RTUs), digital protective relays, and some managed network switches and routers.
A new industrial vulnerability is found every day as a result of defects, incorrect settings, or insufficient maintenance. The majority of newly discovered vulnerabilities listed in ICS advisories continue to involve memory corruption problems. Given that many ICS assets’ software stacks lack inherent security and have little security control, it is likely that this condition will persist.
The threat landscape is expanding daily, and some threats, particularly supply chain and ransomware attacks may develop into disruptive and catastrophic capabilities.
Operations involving ransomware are still very prevalent and indiscriminately target valuable businesses that could be threatened with extortion for money. Here is the outstanding OT landscape, depicted in the below image.

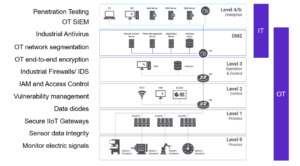
We know that IT/OT convergence is happening at the network, OS, application, and personnel levels; the below image depicts a list of the technical controls that can be implemented within this convergence ecosystem at each layer of the Purdue model.
Given that, building a comprehensive industrial cyber security programme is more important than ever. Compared to previous years, the industrial regulatory spectrum in many geographical areas of the world is becoming more mature. Many countries have drafted their own custom standards as regulatory vehicles based on infamous international standards such as ISO 27001, especially now with the update of ISO 27002:2022 and the seamless integration of GDPR into it, ISA/IEC 62443, and NIST 800-82.
In addition to local, regional, and international standards, which can act as an overarching regulatory umbrella for your program, you need a tactical framework to underpin your journey. What is better than the MITRE ATT&CK for ICS framework to benchmark all your efforts against? This framework provides a map for TTPS that is commonly used by adversaries. Furthermore, this framework can be used by the industrial community as a common language to effectively communicate and analyse incidents, not to mention its impact on improving your organization’s security strategies and policies.
One of the main OT challenges faced by the majority of industrial organisations is asset and network visibility. A recent study conducted by DRAGOS revealed that 90% of their clients had limited or no visibility into their industrial networks. Under many circumstances, network analysts were blind to critical network traffic, and centralised logging was not in place. Identifying your crown jewels and monitoring what is going on in your ICS network are critical steps for developing a full picture of what occurs across industrial assets and sites.
Luckily, there are many products on the market that offer network visibility, threat detection, and operational insight capabilities. Implementing such solutions goes hand in hand with digital transformation and business modernization journeys. Such solutions will enable your cyber security team to deeply monitor the OT environment and create specific use cases to quickly react to suspicious activities. Finally, this can enable and prepare for conversions between IT and OT, which will become a reality as both environments become easier to manage.
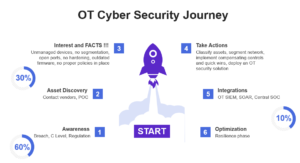
Many companies have not yet implemented such solutions, but why? Well, because of their ways of working, typically for organisational culture reasons. Usually, such companies do not react to a breach, enforcement of a regulation, or a mandate by the C-level or board of directors. 60% of companies are still at this stage. A POC for a specific product has been initiated by 30% of the companies. They have come to know the vulnerabilities they have in their OT environment, and they have started taking some actions to remedy those vulnerabilities. Only 10% of industrial companies are in the optimization phase, which includes a centralised SOC as well as security streamlining and orchestration.
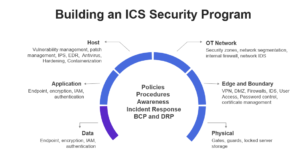
The rule of thumb is “threats can be mitigated through a well-maintained defence in-depth strategy.” Industrial environments are no different. Data, application, host, OT network, edge, and boundary, in addition to physical security layers, must be carefully assessed before relevant security controls can be implemented. The most important factors are the governance aspect and management support, employees’ awareness, and the existence of solid policies and procedures, in addition to having resilient incident response and business continuity plans.
My advice to corporate cyber security teams is to go to their plants, understand the process well, learn the language of the OT people, and build relationships with them, as this will help in tackling cyber security concerns more efficiently.
Also read: It is the best time to invest in technology and make it agile
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics






