The key components of any cyber resilience strategy include Availability, Adaptability, Response and Recovery, durability, threat protection, attack surface management, continuous monitoring, and control assurance
This is an exclusive article series conducted by the Editor Team of CIO News with Kavitha Srinivasulu, Global Head – Cyber Risk & Data Privacy – R&C BFSI at Tata Consultancy Services
About Kavitha Srinivasulu: Kavitha Srinivasulu has around 20 years of experience focused on Cybersecurity, Data privacy, and Business Resilience across BFSI, Financial services, Retail, Manufacturing, Health care, IT services, and Telecom domains. She has demonstrated her core expertise in Risk Advisory, Business consulting, and Delivery assurance with diverse experience across corporate and Strategic Partners. She is a natural leader with the versatility to negotiate and influence at all levels. The views and opinions expressed by Kavitha in this article are only from her personal side and do not represent her company’s viewpoints or any of her customers views.
Cyber resilience is important in today’s evolving threat landscape because traditional security measures are no longer enough to ensure adequate information security, data security, and network security. In fact, many CISOs and IT security teams now assume that attackers will eventually gain unauthorized access to their organizations.
An organization is cyber resilient when it can defend against cyber threats, have adequate cybersecurity risk management, and assure business continuity during and after cyber incidents. However, it’s not only important to enable and improve the current security posture within the organization based on the recent past, but it’s also very important to consider the cyber security assurance across the 3rd parties, 4th parties, Nth parties, and all the other dependent stakeholders who play a major role during an incident or to face the highly demanding legal and regulatory requirements in today’s threat landscape.
The five pillars of Cyber Resilience –
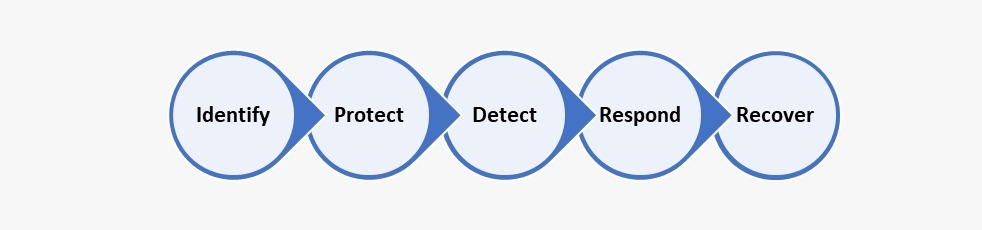
Building cyber resiliency within and outside your organization involves implementing strategies, processes, and technologies to ensure that your organization can continue operating in the face of a cyber incident and collaborating with respective vendors to proactively take measures before it impacts the business. Cyber resilience, alongside attack surface management, has developed significantly over the past few years because the old tradition of building security controls like simulation testing, tabletop exercises, vulnerability assessment, penetration testing, and security assessment is no longer enough to minimize the cyber risk.
Third parties can significantly impact an organization’s cyber resilience, as they often have access to sensitive information, and the systems can introduce new vulnerabilities into an organization’s environment with evolving threats day by day.
Some of the key steps that can be taken to safeguard an organization’s security posture are:
- Identify your most critical third parties with whom you have high dependencies and who pose the most significant risk to you when a data breach or cyber incident occurs in their environment.
- Assess and remediate the identified gaps in a timely manner to ensure the third parties are not vulnerable to any cyber threats.
- Prioritize remediation efforts on the specific areas of concern with your third parties.
- Continuous monitoring and upkeep of industry trends
- Regular communication is crucial to ensuring that your security concerns are addressed in a timely manner.
- Develop an incident response plan, including the steps to take should a third party experience a breach.
- Security controls are regularly tested in the vendor environment, based on which vendor performance and maturity levels are calculated and assessed.
- Vendor Risk Assessment on an annual basis or based on the change should be mandated.
- Access controls should be enabled for need-based purposes only.
- Reporting analytics and Dashboards are published to ensure control assurance.
Cyber resiliency is not only about preventing cyber-attacks or data breaches but also ensuring that an organization or a third party can withstand and recover from them. It also calls out to all organizations in recent times to consider 3rd party security assurance and having the right set of tools and processes in place to make the efforts more efficient and sustain your cyber resilience.
- Build and Protect: It’s important to build a robust security posture to ensure it has the capabilities to identify, assess, and manage cyber risks associated with infrastructure and information systems, including 3rd parties, 4th parties, and Nth parties.
- Manage and Monitor: We need to ensure that the 3rd parties have continuous security monitoring controls in place and that there is an attack surface management process that helps in proactively detecting anomalies and data leaks before any significant damage occurs.
- Respond and Recover: Ensure that the third parties have adequate incident response planning and appropriate controls in place to ensure disaster recovery and business continuity, even if you are the victim of a cyberattack.
- Controls Management and Continuous Assurance: One of the key parameters lies not only in building the security controls but also in ensuring that your cyber resilience program is overseen by the board of Directors and relevant stakeholders.
The key components of any cyber resilience strategy include Availability, Adaptability, Response and Recovery, durability, threat protection, attack surface management, continuous monitoring, and control assurance. Cyber resilience strategies provide a range of benefits before, during, and after cyberattacks, like:
- Enhanced system security.
- Reduced financial loss.
- Reputational Damage is protected.
- Legal and Regulatory compliance
- Technical agility and adaptability.
- Diversity of Cyber capacity.
- Trust between clients and third parties increases.
A cyberattack on a third-party vendor creates cybersecurity, operational, compliance, and reputational risks for all organizations the vendor works with. Dealing with these risks can also result in substantial financial losses. Hence, enabling or developing a cyber resilience strategy is the key component in security scale to proactively prevent and reduce human errors, emerging risks, evolving vulnerabilities, and misconfigurations in the system or applications. The key element of building cyber resilience within the organization and with all third parties is to protect the organization, be ready to face an attack, and respond in a timely manner.
Also read: Unleashing the Power of Machine Learning – Implementation and Implications
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics






