This is an exclusive article series conducted by the Editor Team of CIO News with Kavitha Srinivasulu, Global Head – Cyber Risk & Data Privacy: R&C BFSI – Tata Consultancy Services (TCS).
As we step into the digital era and as technology is evolving day by day, our reliance on mobile devices has reached unprecedented levels. Mobile devices have become one of the daily essentials that act as the central hubs for our personal and professional lives. From managing finances, balancing work, and online purchases to controlling smart home devices, mobile phones play a crucial role in our day-to-day activities. However, this increasing dependency has opened a big door for cyber criminals to hunt for data and create cyber threats. Cybercriminals are constantly evolving their approaches and targeting mobile devices with more sophistication.
More than 40% of organizations give less attention to building cybersecurity measures for their mobile applications. This neglect has increased the risk of data theft, data leakage, data loss, and business regression. The development of new technologies and the trend of mobility have led to a significant rise in cyber incidents across the globe. Therefore, protecting a mobile device from cyber threats is highly important. Unfortunately, certain companies realize the significance of these points only after the actual cyberattacks.
As mobile devices allow us to do everything online with limited dependencies and challenges, it’s become an easy communication tool, including online banking, shopping, and home appliances. While mobile phones may have made our lives easier and more convenient, there has been a rapid increase in mobile threats, and it calls out for new mobile app security standards and measures to protect the data within the mobile devices. Securing applications and data against exploitation is the key focus for most of the companies, as most of the official applications are enabled on mobile devices for ease of use and scalability. The key responsibility of an organization is to secure applications and data against exploitation, whether they are present in a system, laptop, or mobile device. When a mobile app is developed in a small company or a big company, cybersecurity is of utmost importance to keep all users’ data protected and out of reach for predators. Some of the current challenges and emerging threats are:
In 2024, the types of cyber threats targeting mobile devices will be broader and more dangerous. Predators are developing various vulnerabilities in mobile operating systems and apps, making usage of mobile devices more complicated. Concerns are rising about data exploitation on both personal and official applications managed using mobile devices. In mobile apps, the data within the app may be at risk if an organization fails to consider security measures during the app design itself to ensure data protection of the end users. So, developers must be more vigilant while developing apps for both Android and iOS platforms. Securing mobile devices requires a multi-layered approach and investment in enterprise security solutions to safeguard the network. While there are key elements to mobile device security, each organization needs to find what suits best for its network and invest in the right security controls to build a robust cyber security posture.
The core elements of implementing cybersecurity on mobile devices are:
- Store information in device memory (RAM).
- Use EncryptedSharedPreferences, Encrypted Datastore for Android and Keychain, Encrypted RealmSwift, and SQLCipher for iOS.
- Check if the application sessions are closed appropriately.
- Implement SSL-Pinning in the application to avoid internal or external threats.
- Introduce password hashing or full request hashing by creating a request signing token.
- Follow ISO/NIST guidelines for the algorithms used to stay compliant.
- Hide the location of any sensitive pages on the server that may be accessible via the Internet.
- Find dynamic dependencies to take measures to protect these vulnerabilities from attacks.
- Reveal cases of unmanaged code and eliminate the consequences.
- Ensure that the certificate has not expired if the application uses certificate pinning.
- Ensure the application’s business logic is protected and not susceptible to external attacks.
User data is like a ransom for cybercriminals, as they can access anything from personal details to credit card details, including email passwords and user contact lists. Some of the individuals have also been fiddled into downloading malicious adware, and at times, they unknowingly subscribe to fake/fraud-paid services. Therefore, a lapse in any mobile app’s security is a challenging scenario for app owners, developers, and end users. According to a recent survey, more than 60% of companies reported that an insecure mobile app caused a data breach, and 33% out of them had no security controls in place to secure their app against further potential cyber-attacks.
A comprehensive mobile strategy involves not just strategic planning but also identifying and mitigating roadblocks on the path to mobile project development, establishing strategic objectives and KPIs, and choosing the right security tools and technology. Security plays a vital role in using mobile apps, so it’s crucial to use best practices in protecting mobile apps against emerging risks and vulnerabilities growing with the technology.
Some of the best practices are:
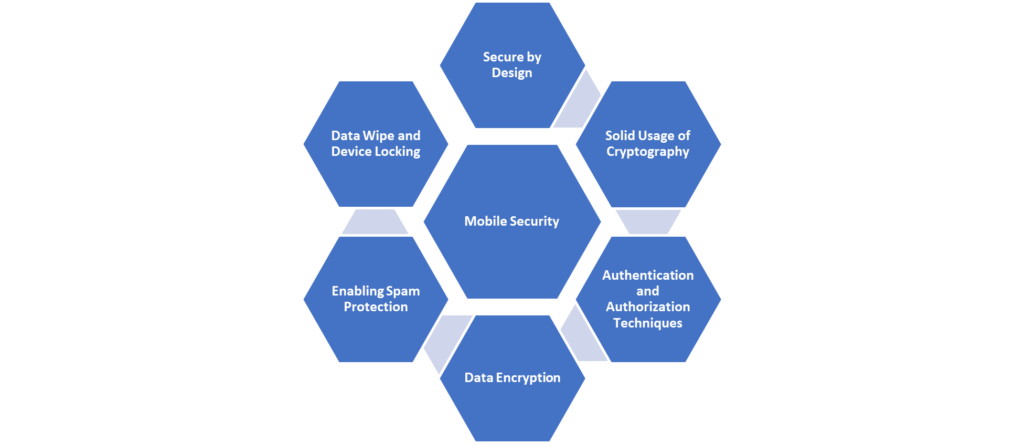
Secure by Design: One of the best approaches is to integrate security measures by embedding controls right from the DNA of a mobile app. We need to evaluate every possible vulnerability or weakness that a predator could exploit and affect mobile apps by a data breach or a ransomware attack. Hence, it is better to build the application by using a secure by design approach.
Solid Usage of Cryptography: Cryptography was originally used to transfer data without revealing the message to the third party. However, encryption and decryption can be enabled of data during transfer. Using a strong data encryption technique, application data such as source code, user info, login credentials, and app storage can be secured from hackers. Once the data is encrypted, even if the hacker steals the data, it becomes difficult to understand the original content.
Authentication and Authorization Techniques: Organizations should consider enabling the right level of access to the right set of people from the development stage itself. Moreover, it is worth making it so that users change their passwords from time to time. It is also recommended to use a multilayered authentication process to login to sensitive or critical mobile applications to avoid unauthorized external access. The lack of such authentication results in security breaches or critical security incidents.
Data encryption: Data transfer from end to end is highly vulnerable from place to place. At this point, predators can steal vital records, influencing the data with weak controls on mobile devices. To avoid such situations, encrypting the data in transit and at rest would help. There are many cryptography techniques now. They are grouped into shared-key cryptography and public-key cryptography algorithms. Depending on the amount of data transferred, the required security measures are applied to simplify and secure the data.
Enabling spam protection: By making the OS more difficult to hack, hardening the OS would increase the application security. For example, Apple has been a leader in making its OS opaque for hackers/predators.
Data Wipe and Device Locking: This feature is mostly used in mobile applications, containing confidential data such as personal, financial, health information, etc. It is a security layer where the remote data is wiped after several unsuccessful login attempts from the user side, and the application is locked.
Conclusion
As the usage of mobile applications has become a daily routine and an important mode of communication for businesses, it is essential to enable robust security measures to stay resilient in protecting the data and customer trust. As mentioned, the mobile app developed with a proper security framework can help to avoid future threats from cybercriminals. When it comes to addressing mobile device security or protection, the level of security around this space is growing, and at the same time, vulnerabilities will continue to deliver a plethora of issues to face. Organizations should apply mobile strategy diligently, making sure security controls are embedded within the app designs and development to minimize risks. It’s time for enabling the right set of security controls and new ways to strengthen the security of core mobile apps against the most common security failures.
About Kavitha Srinivasulu
Kavitha Srinivasulu is an experienced cybersecurity and data privacy leader with over 20 years of experience focused on risk advisory, data protection, and business resilience. She has demonstrated expertise in identifying and mitigating risks across ISO, NIST, SOC, CRS, GRC, RegTech, and emerging technologies, with diverse experience across corporate and strategic partners. She possesses a solid balance of domain knowledge and smart business acumen, ensuring business requirements and organizational goals are met.
Disclaimer: The views and opinions expressed by Kavitha in this article are solely her own and do not represent the views of her company or her customers.
Also read: Automation in Oil and Gas: Horizons and Expectations for the Next 5 Years
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News is the premier platform dedicated to delivering the latest news, updates, and insights from the CIO industry. As a trusted source in the technology and IT sector, we provide a comprehensive resource for executives and professionals seeking to stay informed and ahead of the curve. With a focus on cutting-edge developments and trends, CIO News serves as your go-to destination for staying abreast of the rapidly evolving landscape of technology and IT. Founded in June 2020, CIO News has rapidly evolved with ambitious growth plans to expand globally, targeting markets in the Middle East & Africa, ASEAN, USA, and the UK.
CIO News is a proprietary of Mercadeo Multiventures Pvt Ltd.






