Many of the phishing links seen by Barracuda researchers have the top-level domain “.ru” and are hosted behind a content delivery network (CDN) that acts as a proxy for the source site.
India, December 7, 2023: Barracuda, a leading provider of cloud-first security solutions, has unveiled a new Threat Spotlight in which security researchers at Barracuda are warning of a recent surge in phishing attacks leveraging Adobe InDesign, a known and trusted document publishing system. Some of the attacks are targeted.
According to Barracuda Telemetry, there has been a near 30-fold increase since October in emails carrying Adobe InDesign links. The daily count has jumped from around 75 per day to around 2,000 per day. Almost one in 10 (9%) of these emails carries active phishing links. A further 20% or so includes removed content.
Many of the phishing links seen by Barracuda researchers have the top-level domain “.ru” and are hosted behind a content delivery network (CDN) that acts as a proxy for the source site. This helps to obscure the source of the content and makes it harder for security technologies to detect and block the attacks.
Advanced to very basic attacks
Some of the attacks leveraging Adobe InDesign appear to be targeted at specific organizations or users. These emails carry legitimate brand logos that have probably been copied from other content or scraped from websites by the attackers. The logos are likely to have been chosen because they are known and trusted by the targets—and they suggest the attackers spent time and resources crafting these messages
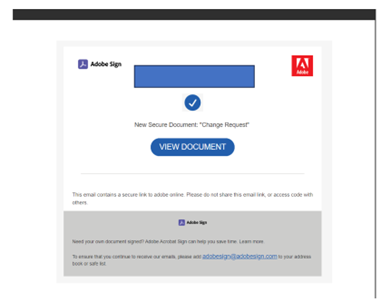
The rest of the attacks are mainly generic mass-distributed messages featuring the OneDrive, SharePoint, and Adobe logos.

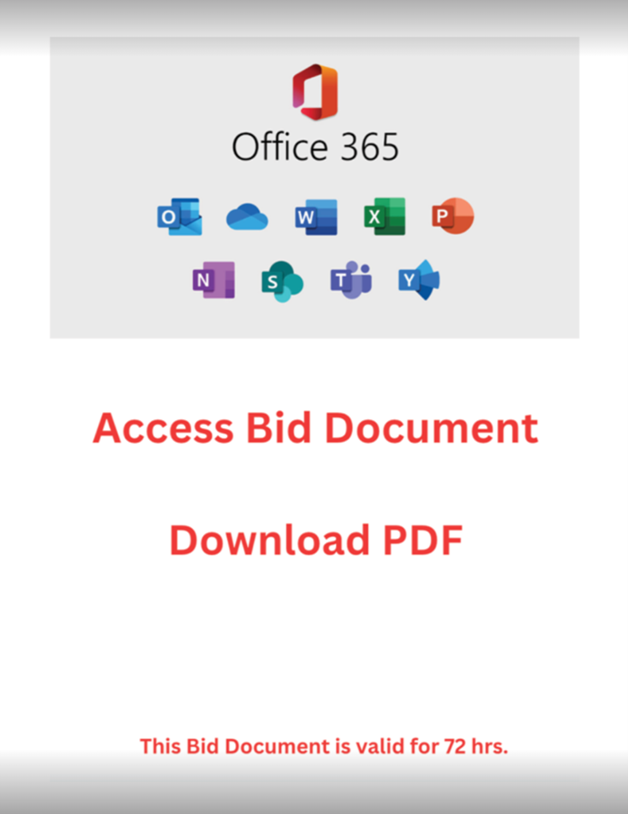
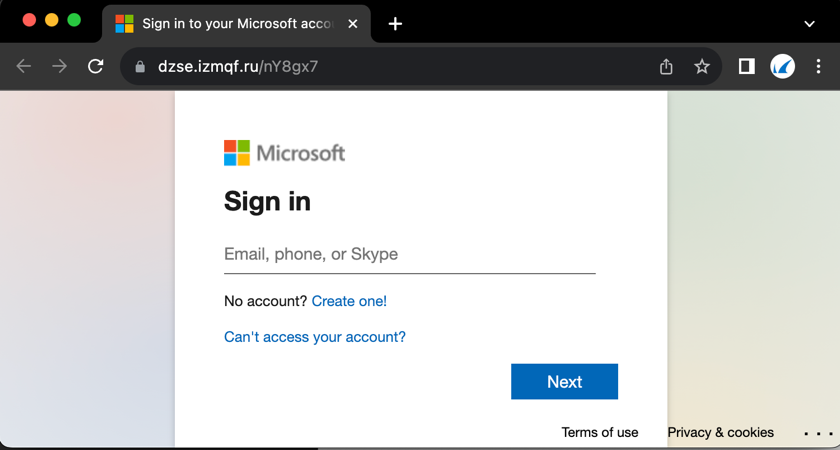
Some feature very basic text, pulled together with minimal effort.
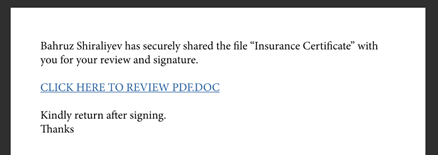
All the attacks are relatively straightforward and consistent in their approach, inviting the recipient to click on a link that will take them to another site, hosted on the indd.adobe[.]com subdomain but actually controlled by the attackers, for the next stage of the attack.
Why do these attacks succeed?
Phishing attacks continue to evolve to become more sophisticated, deploying different techniques and tactics to bypass security detection and trap victims.
The attacks leveraging Adobe InDesign employ several tactics to evade detection and trick targets.
- First, they leverage a known and trusted domain that is not commonly blocklisted.
- Second, by using a publishing program, they can create highly convincing social engineering attacks.
- Third, once the recipient clicks on the link, they are moved to another web page. This means that there is no known malicious URL link in the main body of the message for traditional security tools to detect and block.
- Fourth, for those attacks hosted behind the CDN, this further helps to obscure the malicious source of the content and makes it harder for security technologies to detect and block.
How to stay safe
To stay protected, it is important to have advanced, multilayered, and AI-powered email security in place that is capable of spotting emerging as well as known threats.
This should be accompanied by regular cybersecurity awareness training for employees. The training should be updated whenever new threat trends appear so that employees know what to look out for and what to do if they spot a suspicious or malicious email.
Barracuda’s detection data shows that some of the phishing attacks leveraging Adobe InDesign targeted multiple employees within the same organization, and the rapid reporting of and response to such attacks can stop them in their tracks.
Barracuda LinkProtect
Barracuda Email Protection includes a link protection capability to ensure users do not click on any malicious URLs.
LinkProtect wraps every link in an email that passes through its gateway product, and an analysis is performed at the time of click of every URL to identify if the link is good or bad. In addition, LinkProtect’s ability to act as a protective layer between the email and the recipient is critical because it serves as the last line of defense in case the threat is new or unknown.
For more information, please visit the blog: https://blog.barracuda.com/2023/12/04/threat-spotlight-phishing-emails-adobe-indesign
Also read: Organizations should be driven based on people and processes instead of emphasizing technology
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics.






