An investment in cyber security will pay back a business
This is an exclusive interview conducted by the Editor Team of CIO News with Sanket Sarkar, Founder of ZERON, on quantifying the return on investment (ROI) of cyber security.
When the management asks the CISO: “Hey, we invested $5000 last month on cyber security measures. What’s the return on that?”
A generic reply is, “We saved 30 attacks out of 40 attacks; we saved five data breaches.”
Well, if you ask me, the answer is pretty good, but it can be cooler. Think if you could answer, “Well, we invested $5000; in return, we saved $30,000 worth of losses.”
That’s where quantification of cyber security to a micro-economics level comes into the picture.
Return on Investment (ROI) is probably the single most important metric when it comes to business. It answers the question, “For every dollar invested, what do I get back?” In profit-generating areas like sales, it’s fairly easy to calculate ROI because it’s just Revenue – Cost = Profit. However, cyber security is a cost center, meaning it doesn’t generate profit for the business, so it’s a bit harder to calculate the ROI, but it’s not impossible.
There are many methodologies, but here I would be focusing on SLE.
Single Loss Expectancy [SLE] methodology
SLE is the estimate of the amount of damage that an asset will suffer due to a single incident.
Asset categories include people, facilities, equipment, materials, information, activities, and operations.
The following formula is used to calculate the single loss expectancy: Single Loss Expectancy = Asset Value * Exposure Factor
The exposure factor (EF) is expressed as a percentage of the asset value. If loss can be limited to one type, the impact on the asset by the percentage of the asset value lost can be determined.
This means that an investment in cyber security will pay back a business. Anytime the company suffers some type of security breach, there is a cost associated with that. So, by reducing the rate of occurrence for a specific type of incident, you save the company money. For example, say company “X” suffers seven data breaches a year because of phishing emails that cost $13,000 to fix (7 X 13,000 = $91,000 per year). To fix this, you implement a security control that costs you $25,000 but reduces the rate of occurrence by half, saving you $60,000 per year.
Your payback in the first year alone will be 60,000-25,000 = $35,000. This is one way a cyber security initiative can have a measurable ROI by looking at the annual rate of occurrence, calculating the expected decrease in rate of occurrence, and subtracting the amount of the control. Controls can be technical things like a firewall, but they can also be hiring additional staff to do training or to respond to and contain situations as they occur.
Some statistics show how cyber security is getting more time in boardrooms. And the thing that matters most to the board members is the “MONEY”.
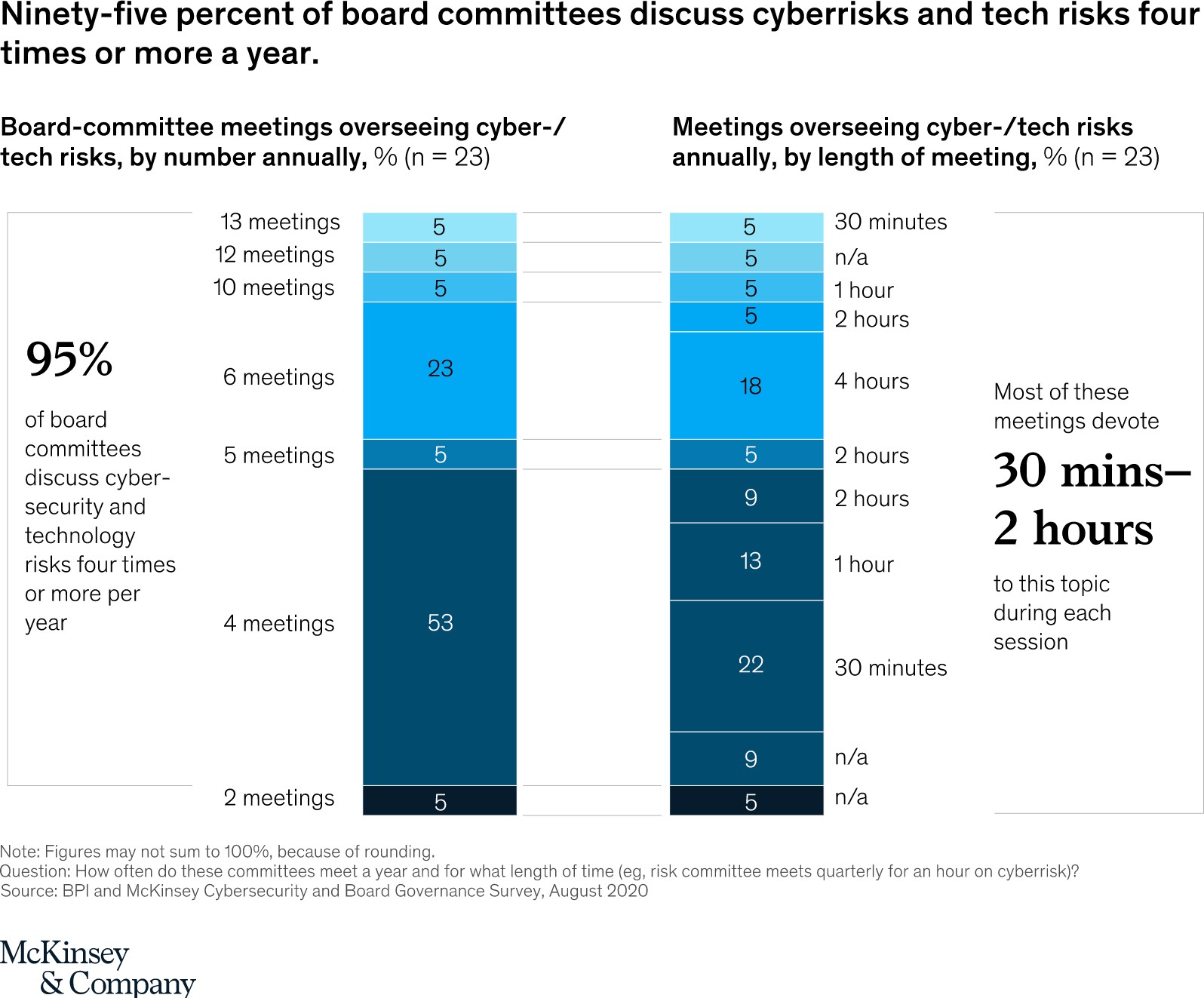
It’s pretty much clear that CISOs should have systems in place that can give them an understanding of the ROI of their investments.
Also read: CIO News interviews Shri Wangki Lowang, Minister (IT) of Arunachal Pradesh
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics






