A new posture for cybersecurity in a networked world” explains how companies can use organisational structure and governance to enhance cybersecurity
This is an exclusive interview conducted by Santosh Vaswani, Editor at CIO News with Kapil Bareja, Advisory Board Member at Cyber Security Tribe
It wasn’t too long ago that sophisticated executives could have long, thoughtful discussions on technology strategy without even mentioning security. Today, companies have substantial assets and value manifested in digital form, and they are deeply connected to global technology networks, even as cyber attackers become ever more sophisticated and adaptable to defences. At most companies, boards and senior executives acknowledge the serious threats that cyberattacks pose to their businesses. What they are not sure of is how to create a strategy that helps them understand and address the threats in all their forms today and in the years ahead. And they’re asking for such a strategy every day. Our experience working to protect some of the world’s largest and most sophisticated companies and our proprietary research have revealed three broad mandates that can help organisations transform their cybersecurity efforts. In this compendium, we offer a comprehensive series of articles that describe how companies can make these mandates a reality and help their leaders sleep more soundly.
Go beyond technical controls to build a holistic programme that protects the enterprise.
“Hit or myth? Understanding the true costs and impact of cybersecurity programmes” shows that more spending doesn’t necessarily lead to better
“A new posture for cybersecurity in a networked world” explains how companies can use organisational structure and governance to enhance cybersecurity.
“Protecting your critical digital assets: not all systems are created equal” shows that companies must focus their strongest protections on their most important systems and
“Insider Threat: The Human Elements of CyberRisk” discusses how to use targeted analytics to eliminate threats from adversaries within the organisation.
“To survive in the age of advanced cyberthreats, use ‘active defence,” which explains how to respond to emerging attacks by applying threat intelligence and
“Making a secure transition to the public cloud” reveals how leading-edge companies are exploiting the opportunities of public cloud infrastructure while they build the processes, architectures, and operating models necessary to protect sensitive
“CyberRisk measurement and the holistic cybersecurity approach”. Comprehensive dashboards can accurately identify, size, and prioritise cyberthreats.
“Cybersecurity and the Risk Function” Information technology, cybersecurity, and risk professionals need to work together to protect their organisations from
Engage the full set of stakeholders to ensure appropriate support and decision-making.
“A Framework for Improving Cybersecurity Discussions within Organisations” explains tangible mechanisms the chief information security officer can use to gain buy-in throughout the company and improve decision-making.
“The board’s role in managing cybersecurity risks” lays out what cybersecurity data the board of directors should expect and the questions it should ask.
“Asking the right questions to define the government’s role in cybersecurity” provides a framework for how public policymakers can think about engaging constructively in cybersecurity.
Integrate cybersecurity with business strategy to build trust and create value.
“How CEOs can tackle the challenge of cybersecurity in the age of the Internet of Things,” shows how companies can engineer security into IoT products.
“Shifting gears in cybersecurity for connected cars” makes the case for automakers to start investing in security design to protect themselves and the people who drive their vehicles.
“Critical Resilience: Adapting Infrastructure to Resist Cyberthreats” highlights the mindset shifts required for managers in physical infrastructure companies.
A new posture for cybersecurity in a networked world
As the dangers mount, current approaches aren’t working. Cyberrisk management needs a root-and-branch overhaul.
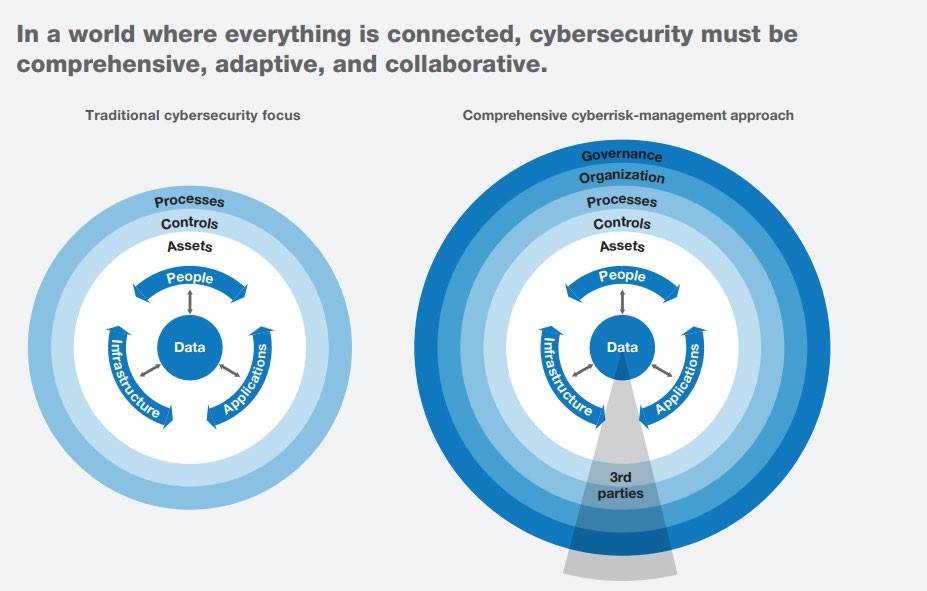
To prepare global companies for an age of all-encompassing connectivity, executives need a more adaptive, thorough, and collaborative approach to cyberrisk (Exhibit 1). We have observed the following principles used by some of the world’s leading cybersecurity teams at global companies:
Cyberrisk needs to be treated as a risk management issue, not an IT problem. Cyberrisk is much like any other complex, critical, nonfinancial risk. Key elements of its management include the prioritisation of relevant threats, the determination of a company’s risk appetite (its willingness to accept some risk), and the definition of initiatives to minimise risk. Additionally, companies need to put in place an organisational structure and a governance approach that bring transparency and enable real-time risk management.
Companies must address cybersecurity risks in a business context. Technical experts cannot solve the problem without understanding the underlying commercial and organisational requirements. Companies tend to overinvest in technical gadgets and underinvest in complexity reduction and consistent coverage of their whole value chain, such as vendor risk management. The result is an inefficient system.
Companies must seek out and mitigate cyberrisk on many levels. Data, infrastructure, applications, and people are exposed to different threat types and levels. Creating a comprehensive register of all these assets is tedious and time-consuming. Companies should take advantage of automated tools to catalogue their assets, the better to focus on those at greatest risk.
Adaptation is essential. Sooner or later, every organization will be affected by a cyberattack. A company’s organisation, processes, IT, OT, and products need to be reviewed and adjusted as cyberthreats evolve. In particular, companies must fine-tune business continuity and crisis management structures and processes to meet changes in the threat level.
Cyberrisk calls for comprehensive, collaborative governance. Traditionally, many companies distinguish between physical and information security, between IT and OT, between business continuity management and data protection, and between in-house and external security. In the digital age, these splits are obsolete. Scattered responsibility can put the entire organisation at risk. To reduce redundancies, speed up responses, and boost overall resilience, companies need to address all parts of the business affected by cyberthreats—that is, all parts of the business, and suppliers and customers too. While it may be hard—or even impossible—to protect a company against the most advanced attacks, systematic governance is the best insurance against the bulk of everyday attacks.
Exhibit 1
The new approach also makes better use of cybersecurity resources and funds. Just refocusing investment on truly crucial assets can save up to 20 percent of cybersecurity costs. In my experience, up to 50 percent of a company’s systems are not critical from a cybersecurity perspective. We’ve also seen that the cost of implementing a given security solution can vary by a factor of five between comparable companies, suggesting that many companies are missing out on considerable efficiencies.
Also read: Automate People and Process Management with greytHR
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics






