
A common approach to maintaining security while handling remote traffic is to backhaul all application and internet traffic through the corporate data centre for verification before it reaches its destination
When asked how he planned his career path to be a successful technology leader, Anthony Lim, Director, Cyber Managed Ops & Project Chief Security Officer at NCS Group, in an exclusive interview with CIO News, said, in my case:
(a) I was always on the lookout for and researching what I perceived to be the next important area in cyber-security and technology. There are so many of them and we can’t be everywhere, so we need to pick our fights. Begin with a broad, high-level domain at a time, such as cloud, smart cities/nations, OT/ICS, and governance (as I did). Then within each, home in on one or two specific areas.
(b) I looked for something I like, whether it’s a domain, a product, a solution, or a technology. If I like something, then my passion and motivation will be higher, so the intention, effort and capacity will be successful. You have got to feel like you invented this thing, not just deal with it for a job. Then you will believe it and articulate the propositions better and more convincingly.
When asked about challenges he faced in his career path and how he overcame them, he said, firstly, having said per above, it is more often than not challenging to find a new solution, technology, or domain area you can believe in and get passionate about easily (you can’t do it for the sake of doing so). And it is not just about how one feels – we must conduct research, speak with people, and read industry trends reports. Many had “bet on the wrong horses.”
The other challenge (not always a bad thing) is how we align and balance our thoughts and messaging with that of the respective vendor’s or solution-provider we are working for. Especially today, it becomes too easy to get caught up in “buzz words” and everyone suddenly hops on the bandwagon like they have something for everyone. Examples include stateful inspection, penetration testing, kill-chain, SDN, and more recently, sandbox, SD-WAN, Zero-Trust, SASE, Threat Intelligence, and so on. We believe in the solution proposition, not the hype in the industry about the matter.
When asked how his organisation geared up in terms of technology in the COVID times, he said, there are 2 areas here:
Firstly, to help gear up the staff and the office network and systems to be able to cope with the now-more-diversified workloads, even though we had been flexible, remote and global for the most part prior to the pandemic lock-down.
Some companies even give staff some money to buy appropriate equipment for their respective homes to help facilitate a better W.F.H. experience – e.g., headphones (for all the zoom/team calls), computer monitors, even ergonomic office chairs (for all the long hours seated at desks) and even desks/tables in some cases. Others offer subsidies for home broadband service, etc.
Back at the office, there is a re-jig of the network architecture to cope now with the influx of many users from outside the office/LAN accessing the office’s IT resources and servers. Many companies have deployed, in a great way, cloud services to meet all their needs – so there has been, thanks to the pandemic, an accelerated business boom for cloud services, cloud service providers, and the data centers that go with it.
Secondly, to gear up the cyber-security of the network and other digital assets, e.g., data, because of the sudden change in configuration of the network, with most or all of the staff now working from home instead of at the office. They are no longer on the office LAN behind the office firewall.
While the company cannot dictate or facilitate the cyber-security posture of each employee’s home internet broadband connection, they can ensure stronger endpoint security solutions, pushed down from and monitored by the corporate IT (or subcontracted cloud service for this), better authentication and network/server/IT resources/services/IT assets protection, using network segmentation, micro-segmentation, threat monitoring and behaviour analytics solutions, etc., to ensure only the appropriate users are accessing the appropriate IT resources and services, now from outside of the LAN. The IT security governance, business continuity, and incident response processes also have to be updated to meet the new diversified IT map.
The ironic challenge to the IT leaders is how to not over-secure the staff endpoints to the extent of demoralising them because if the laptop becomes too hard to use or corporate IT assets become too hard to access, we start to lose productivity (whereas in the office, on the LAN and behind the corporate firewall, often it is easier to use the IT resources as there is no need for individual additional layers of security and authentication).
W.F.H. and remote-access work has been around for many years for many staff, e.g. mobile, sales, and travelling staff, but not in one go for everyone in the building now. Also, in the past, staff W.F.H. when they wanted or needed to, but not enforced permanently.
There are many articles we can read about the cyber-security issues, considerations, and mitigations for a sudden, ad-hoc “new-normal” en-masse work-from-home business IT infrastructure.
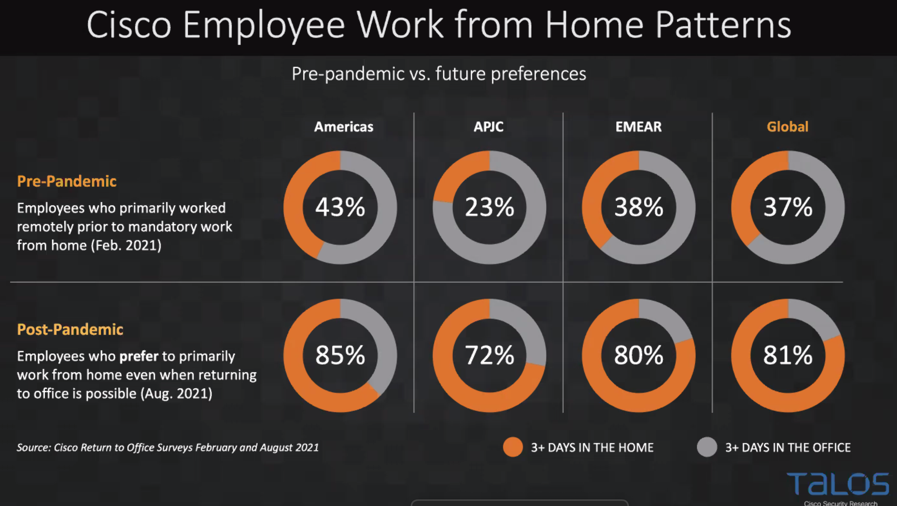
When asked about technology solutions and innovations he plans to implement in the post-COVID era, he said, “There are also many articles now about how, despite the pandemic conditions now easing off around the world, many companies, and many staff as well, are now getting quite used to working around the clock, partly due to uncertainties as to when the virus might erupt again and/or in yet another scary, contagious variant.” So, for now at least, for the sake of safety for all staff, work will minimise co-mingling, whether inadvertent or due to the work activity.
As a result, many of the remote and cloud IT (and the associated re-jigged security IT network architectures, solutions, and services) will remain in place. It is not useful to start dismantling these and switch back to the pre-COVID IT architecture.
Anyway, nowadays it’s much easier to do so if needed, as a lot of architecture configurations are now software-defined or software-driven – it started with SDN (software-defined networks), then we have SDDC (software-defined data centers), SD-WAN (software-defined wire-area-network) etc.
Thus, whether as a contingency or a “new normal,” the distributed, diverse, remote, and work pattern, as well as the accompanying re-jigged IT network infrastructure, services, and cyber-security, will persist. Over time, studies will continue to monitor work patterns and any new cyber-security solutions deemed suitable or useful, e.g., external threat intelligence and external attack surface management.
There could be a slight shift in the remote, diversified work pattern as the pandemic restrictions start to let up, as people start to get out (and want/need to get out) — so suddenly all the cafes and WeWork-type virtual office services get a lot of patronage. A good number of companies will have lived out their leases through the past 2 years of pandemic lockdown and are up for renewal now. They are deciding to ditch a lot of the expensive downtown-city posh skyscraper-tower real estate, reducing their office space from, say, 10 floors to just keeping a couple for the address and for some HQ/corp admin functions like top mgmt., board room, accounting, HR, sales operations, client executive showroom, etc. They will:
- Rent another smaller, cheaper place on the outskirts for any required business operations and support needs, and some hot desks for ad hoc staff usage in the area, or who need to have a meeting, conference call room, training, printing, etc.
- Have a regional or national subscription to WeWork, Regus, or another virtual-physical office service for their employees to drop by at this or that branch to do some work, have a client meeting, print something, make a call, and so on.
- Continue to allow most, if not all (depending on role, task, or site resource required) to W.F.H. by default, with the option of several ad hoc work spaces as described above. Sales staff has long been, by default, flexible and mobile anyway.
- In between, staff may want to drop by at a Starbucks or similar for a coffee, do a bit of work there for a bit, or have a client meeting too. This is nothing new but adds to the post-new-normal work flexibility.
(And the cyber-security folks will need to continue to be up-to-date and cope with securing this new ‘millenia-style’ work profile, depending a lot on public and service-provider IT connectivity). We can’t go firewall Starbucks’ or WeWork’s internet connections, but we can ensure our staff connections and office-resource accesses are properly secured.
As you can imagine, the big developers, owners, and landlords of the city’s super tall posh office towers are now panicking because many of their big clients with several floors of office space each are now downsizing to a floor or two each, causing hundreds of thousands or millions in rental revenue to be lost. The developers and landlords, thus too, need to reinvent themselves to stay relevant, if not ahead of their clients’ “new normal” work mode.
When asked about challenges faced by technology leaders today in a similar industry while implementing digital technologies and how technology leaders can overcome the challenges, he said, it’s basically a big paradigm change in securing the new distributed staff IT network.
Here are some ideas about this:
(With thanks to my colleagues at Crowdstrike and Fortinet.)
While cybersecurity professionals continue to make huge strides in protecting organizations, all the technology in the world can’t completely protect users and assets — it also requires caution and constant vigilance by everyone. This is also the stark reality of the current COVID-19 crisis. With so many companies forced to quickly transition to a remote workforce, remaining cautious, vigilant, and informed must be the mantra for all of us.
It should come as no surprise that our adversaries seek to exploit one of our basic human conditions: fear. Right now, we are vulnerable—and our adversaries know it. In a crisis, people tend to lose sight of their better judgment. Meanwhile, criminal hackers and scammers are eager to take advantage of us.
Social engineering attacks have also sought to take advantage of the recent rise in remote employees. The risk of social engineering increases when more employees work from home. It’s easier to fool unsuspecting employees who now have limited face-to-face interaction with their coworkers. That call from “IT” might not be who you think it is. And that email from “Apple” may not come from where you’d expect. Stop and think—ask yourself if the person on the other end of the phone or computer is who they claim to be.
Security awareness is the best way to prevent being victimized. It’s important to be cognizant of common social engineering tactics in order to spot the signs of targeting. Make sure your company has a process in place to allow employees to engage IT security personnel if they have any reason to believe they might be the victims of a social engineering attack.
Three Key IT Pain Points in WFA Models:
Ideally, accessing corporate applications and data from anywhere should be seamless, but remote connectivity often impacts the user experience and security posture. Resolving these issues requires addressing three key IT pain points.
- Unpredictable Experience:
A common approach to maintaining security while handling remote traffic is to backhaul all application and internet traffic through the corporate data centre for verification before it reaches its destination. However, this increases latency and wastes bandwidth compared to a direct connection. Such architectures can also be complex and expensive to operate because IT must individually configure and manage branch routers and stitch firewall policies.
Because of this, QoE (Quality of Experience) becomes inconsistent for branch end-users because backhauling application traffic can impact application reliability. Home users are forced to access applications through a VPN tunnel to the corporate network, leading to even more unpredictability due to variations in home bandwidth capabilities.
Challenges remain even when organisations allow direct access to cloud applications because the improved application experience comes at the cost of security. Home users must also still use a VPN to access internal resources, making their overall experience inconsistent.
- Inconsistent Policies:
IT teams find it challenging to ensure consistent policy enforcement across the network when different sets of security are deployed on-site, at the branch office, in the cloud, and at home locations. This is because an overall lack of visibility and control creates a landscape ripe for threats to leak through. In fact, threat researchers have recently detected a shift in threat actor behaviour aimed at exploiting policy inconsistencies by targeting homes or smaller branch offices rather than attacking traditional network devices. These bad actors can access a device deployed in an under-secured network and use it to hijack a VPN connection back to corporate resources rather than having to force their way past commercial-grade security.
- Implicit Trust:
Many organisations use an implicit trust model when providing access to applications. Those using a VPN connection are usually authenticated with a generic process that provides access to the entire network, with the assumption being that any device connecting through a secure VPN tunnel is to be trusted. But all it takes is for a remote user’s machine, identity, or credentials to become compromised for an attacker to use that trusted VPN connection to gain access to the entire network.
Meeting WFA Challenges with SD-WAN and ZTNA
(Work from anywhere):
When implementing a WFA model, organisations must adapt their existing infrastructures and security models—traditional security and connectivity solutions are simply not up to the task. The good news is that the challenges described above can be met with the deployment of Secure SD-WAN and Zero Trust Network Access (ZTNA) solutions.
While SD-WAN are great at providing reliable connections to cloud-based applications, most SD-WAN solutions lack integrated security. In contrast, Secure SD-WAN on a purpose-built security platform blends advanced connectivity with enterprise-grade security and allows for single-console management, enabling consistent policy creation, deployment, and enforcement. Further, ZTNA provides per-user access to specific applications, far surpassing implicit trust when it comes to security. Regardless of where they are connected, every device, user, and application can be seen and controlled. Together, solutions like Secure SD-WAN and ZTNA help businesses meet the challenges and realize the opportunities that WFA provides.
Also read: CIO News interviews Shri Wangki Lowang, Minister (IT) of Arunachal Pradesh
Do Follow: CIO News LinkedIn Account | CIO News Facebook | CIO News Youtube | CIO News Twitter
About us:
CIO News, a proprietary of Mercadeo, produces award-winning content and resources for IT leaders across any industry through print articles and recorded video interviews on topics in the technology sector such as Digital Transformation, Artificial Intelligence (AI), Machine Learning (ML), Cloud, Robotics, Cyber-security, Data, Analytics, SOC, SASE, among other technology topics





